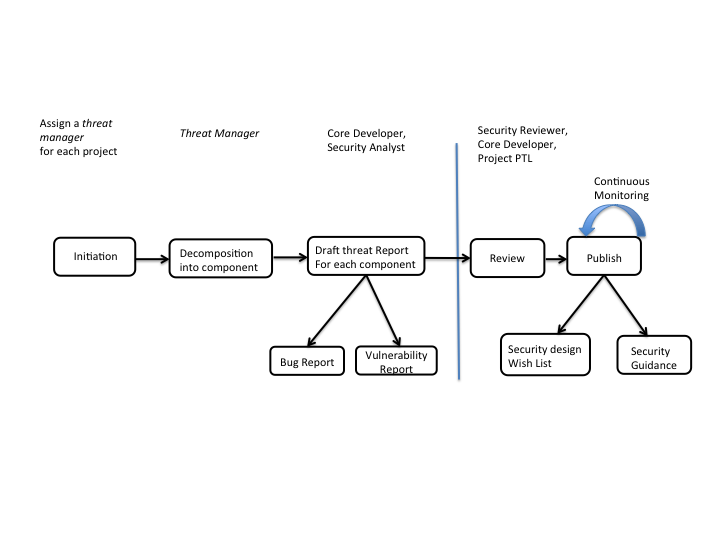
Security/Threat Analysis/process
Contents
OpenStack Threat Modelling Process
Initiation
At the beginning a new 'Threat Manager' ( one responsible for overall management of the work) for each OpenStack project is selected.
Decomposition Into Component
'Threat Manager' performs initial analysis about the target project, do component break down of the project, gather information about the developers / reviewers relevant for each component. In this phase, 'Threat Manager' communicates the ongoing activity to the target project's core developers.
Draft threat Report For each component
'Threat Manager' or an assigned security analyst together with a relevant core developer/s of a project analyses each component ( DFD, Security assumptions, assets identification.. for details check the Threat Modelling process ) and identify possible threats / security weakness in the target component. In addition to the threat report, two possible outcomes are bug notification and vulnerability report to the target project.
Review
The review should be an open review consisting of target project core developers and Security Reviewers. At least two reviews outside authors of draft threat report is required. Reviewing could be performed in GIT ( possibly with gerrit system .. to be decided later). An alternative approach would be, a fast track review process with a dedicated group.
Publish
Threat modelling report is published as a security guidance (either in wiki or in Security Guide Book). Some concrete security wish list / design guidance is submitted to the target project for further improvement.