Neutron/mcafee-ngfw-firewall
Contents
Overview
McAfee NGFW FWaaS integration implements L3 router and FWaaS functionality with the McAfee Next Generation Firewall (NGFW) virtual appliance (VM) and the Security Management Center (SMC) server.
Features
Basic routing
- NGFW routes traffic between networks it is connected to.
External gateway
- You can attach a gateway to the router that works as a default gateway.
Floating IP
- You can associate a public IP to an internal instance with destination NAT.
FWaaS
- You can create FW policy and associate it with all the tenant’s routers.
NGFW features
- You can use the SMC to configure deep packet inspection and application detection rules around the basic firewall policy defined though Neutron.
Architecture
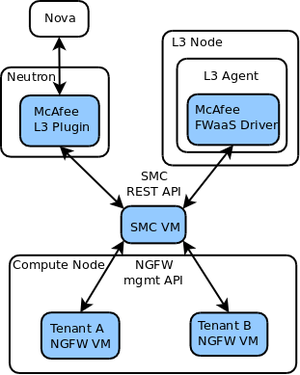
McAfee NGFW FWaaS integration is implemented in two parts: McAfee L3 router plugin and McAfee FWaaS driver.
McAfee L3 router plugin
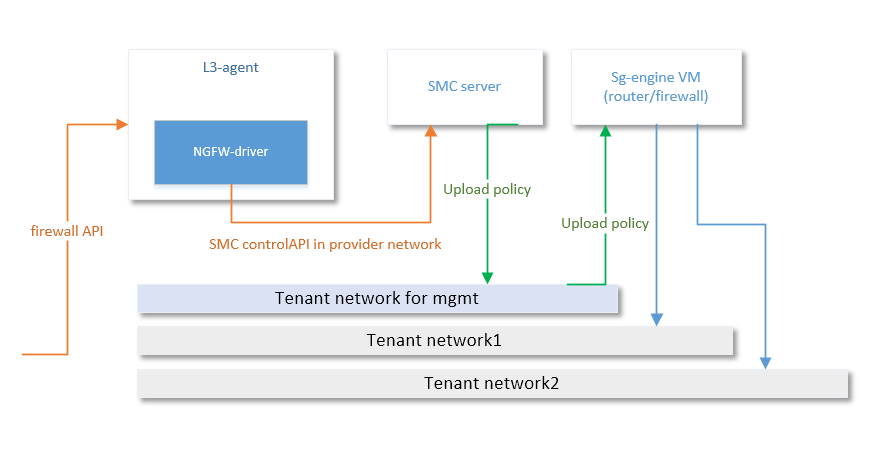
The L3 plugin runs inside Neutron and replaces the upstream network namespace implementation with a router VM. The plugin communicates with Nova to instantiate the VM and attach router ports as they are configured. The NGFW interface and routing configuration is communicated to the pre-configured common SMC server using the SMC REST API. SMC then configures the NGFW VMs.
When created, the router VM is attached to a pre-configured management network that is used for communication between the SMC and NGFW VMs.
The plugin uses two new tables in neutron database to keep track of router VM related information. You can create the tables with mfe-neutron-db-manage command that is a wrapper for neutron-db-manage. McAfee L3 plugin uses its own alembic migration table and thus functions independently of neutron. Make sure to run
mfe-neutron-db-manage upgrade
command each time you update the mfe_fwaas python package.
McAfee FWaaS driver
The FWaaS driver runs inside the L3 agent and conforms to the FwaasDriverBase API. The driver is responsible for translating Neutron firewall object into NGFW policies and applying those policies to the NGFW VMs. Like the L3 plugin, the FWaaS driver consumes the SMC REST API.
Configuration
The current implementation is developed and tested on top of kilo release. You do need to backport the fix for bug #1475244, though.
McAfee L3 router plugin
Install mfe_fwaas python package
pip install mfe_fwaas
Update the Neutron database
mfe-neutron-db-manage upgrade head
As admin, create a tenant for hosting the router VMs
tenant-create --name ngfw_tenant
As admin, create a user for administering the router VMs
keystone user-create --name ngfw_admin --tenant ngfw_tenant --pass password
As admin, make the user admin
keystone user-role-add --user ngfw_admin --tenant ngfw_tenant --role admin
Use the ngfw_admin and ngfw_tenant as the user and project from now on.
Create flavor for the NGFW VM. These resources are the recommended minimums.
nova flavor-create --is-public false ngfw_flavor auto 2048 0 2
Import the NGFW disk image. NOTE: The FWaaS integration requires currently unreleased NGFW features to work properly. Contact McAfee sales for an image.
glance image-create --name ngfw_image --disk-format qcow2 --container-format bare --is-public false --file mcafee_ngfw.img
Create a Neutron network for communication between the SMC and the NGFW firewall VMs. E.g this creates provider network that maps to bridge ‘smc’ to which the SMC server is connected.
neutron net-create --provider:network_type flat --provider:physical_network smc ngfw_mgmt_network
Create a subnet for SMC
neutron subnet-create ngfw_mgmt_network 192.168.206.128/26
Install SMC in a machine that can communicate with both Neutron and the L3 agent as well as the management network. Use the SMC management client to enable the SMC API.
Make sure McAfee router plugin and FWaaS plugin are added to your service plugins in neutron.conf.
service_plugins = mfe_fwaas.router_plugin.ngfw_neutron_plugin.NgfwRouterPlugin,neutron_fwaas.services.firewall.fwaas_plugin.FirewallPlugin
Add the following configuration section to your neutron.conf.
[NGFW] # Router VM parameters ngfw_image_id = 068185a4-20af-43e4-bb89-2e944d4cfe99 ngfw_flavor_id = 044f3971-6cfc-4432-a162-d43a2f58ce62 ngfw_mgmt_network_id = 3f9a2e58-0766-4eca-b5ff-3eb4b2db9cfb vm_spawn_timeout = 0 vm_status_polling_interval = 3 fw_status_polling_interval = 3 fw_status_polling_timeout = 0 # Tenant that owns the router VMs tenant_id = 87e36f304f8a4afdaa989b300100b2e4 tenant_name = ngfw_tenant # Router VM admin user tenant_admin_password = password tenant_admin_name = ngfw_admin # All router VM MACs will start with this. Hotplugging only works with ‘58:7a:4d’. mac_address_prefix = 58:7a:4d # SMC credential smc_api_version = 5.8 smc_url = http://192.168.206.171:8082 smc_api_auth_key = BRTcfZspkFgsoTHcjD680001
McAfee FWaaS driver
After configuring the McAfee L3 plugin, the FWaaS driver is enabled by configuring the following variables in the fwaas_driver.ini.
driver = mfe_fwaas.fwaas_driver.ngfw_fwaas.NgfwFwaasDriver [ngfw] smc_api_auth_key = BRTcfZspkFgsoTHcjD680001 smc_api_version = 5.8 smc_url = http://192.168.206.171:8082