Trusted-Location-Control
Contents
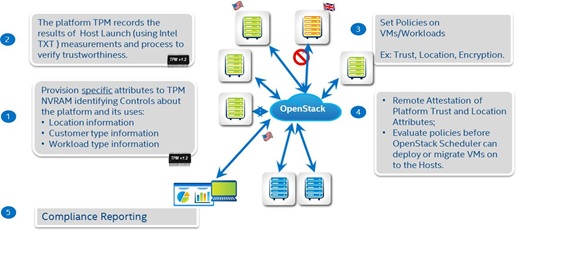
Hardware assisted Geo and Asset Tagging
While the cloud enables workloads and data to reside anywhere, users may be constrained to run their workloads and save their data in certain geographies due to regulatory requirements. This solution will extend to include trusting the location and boundary of the hardware resources, extending the current functionality of trusting the integrality of the compute platform to be free of malware and rootkits. Extensions from this solution enable associating geo and asset tags with hardware at provision time. Intel Trusted Execution Environment (TXT) and other measured launch environments (MLEs) facilitate measurement of provision time information into the Trusted Platform Module (TPM). Remote attestation services can then be used to ascertain that provision time meta-data have not been tampered. Geo and Asset tagging builds on the Trusted Compute Pools feature, covered in TrustedComputingPools
This blueprint details how geo and asset tagging can be incorporated and taken advantage of in OpenStack clouds to provide location and boundary control of workloads/OpenStack images. With Geo/Asset Tags, you can enforce policies to control placement, migration or bursting of workloads to trusted systems in specific geographical locations or boundaries, provide visibility and compliance of your workload policies to ensure tenants that of its compliance to Trust and location policies.
Principles of Operation
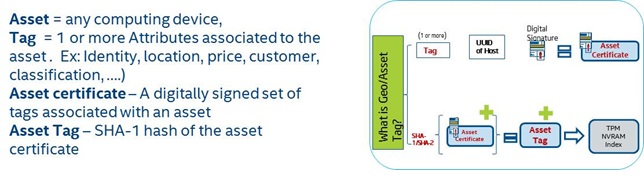
What is Geo/Asset Tag?
Proposed Changes
Geo and Asset Tagging Solution
- Provision geo tags to Compute Hosts using ‘Remote Attestation solution’
- Create a tag or tags
- Create a selection ID by selecting one or more tags
- Provision a selection ID to the asset (ex: Compute Host). The Provisioning process will include generation of Asset Certificate and writing the SHA1 of the certificate to TPM’s NVRAM
- Reboot the host to complete the provisioning process, which will extend the hash to PCR 22 register of TPM.
- For more details follow the instructions in Remote Attestation Solution product guide.
- Create and Add Geo-Location/Asset-tag Policies to VM Image Properties in ‘Open Stack’
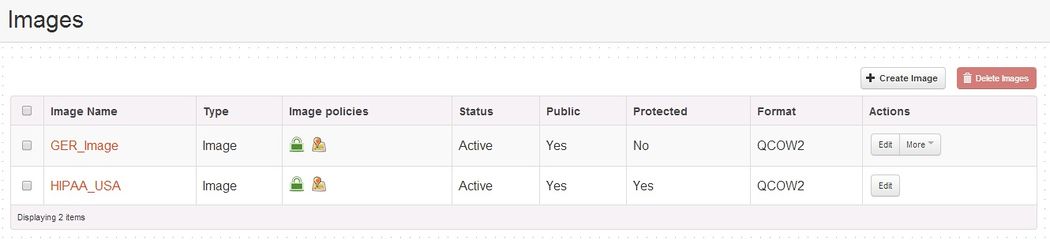
- The following changes have been made to the Images page under the Admin tab.
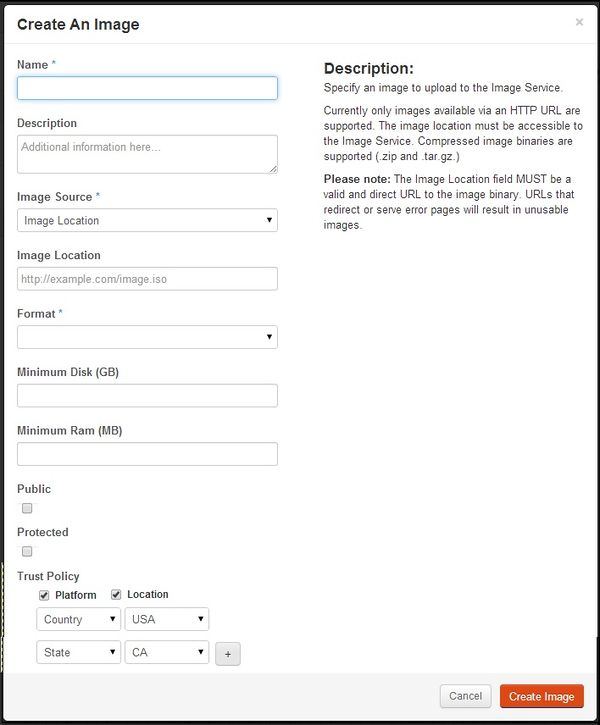
- Display of Trust Policies assigned to each Image.
- Trust Policies can be created and edited in the ‘Create Image’ tab and ‘Edit’ function for each Image.
- Trust Policies, for now, include Platform Integrity and Location and in the future will include VM Integrity.
- Trust Policies and related information as stored as Image properties in the glance database.
- If Trust Policy for Location is selected, Platform Integrity is automatically selected.
- When selecting the Location Trust; user will have option to create policy of one or more of the 5 Key name and value pairs.
- 5 key names include: Country, State, City. Region and Classification.
- Acceptable values for each Key Name will need to be selected from a drop down list. The acceptable values are fetched from the ‘Remote Attestation Solution’
- Below are screen shots of changes that displays ‘Trust Policies’ assigned to each image and Trust Policy creation/edit function in the Update Image page.
- The following changes have been made to the Images page under the Admin tab.
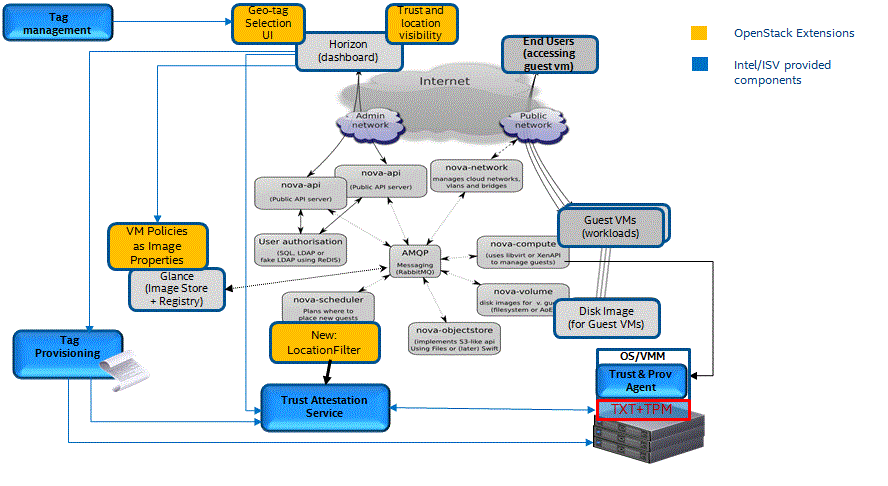
- Asset/Location Filter in Scheduler to orchestrate and control ‘Trust Policies’.
- When a user selects an image to be launched for an instance, the scheduler retrieves the ‘Trust Policy’ for the Glance database
- Scheduler iterates through the available host and fetches the SAML assertion from the ‘Remote Attestation Service’ using Restful API.
- SAML Assertion is parsed to determine match to the ‘Trust Policy’ and once these iterations are completed, scheduler will complete the remaining filter operation and then picks the best ranked host to launch the instance.
- Trust Visibility within OpenStack Horizon
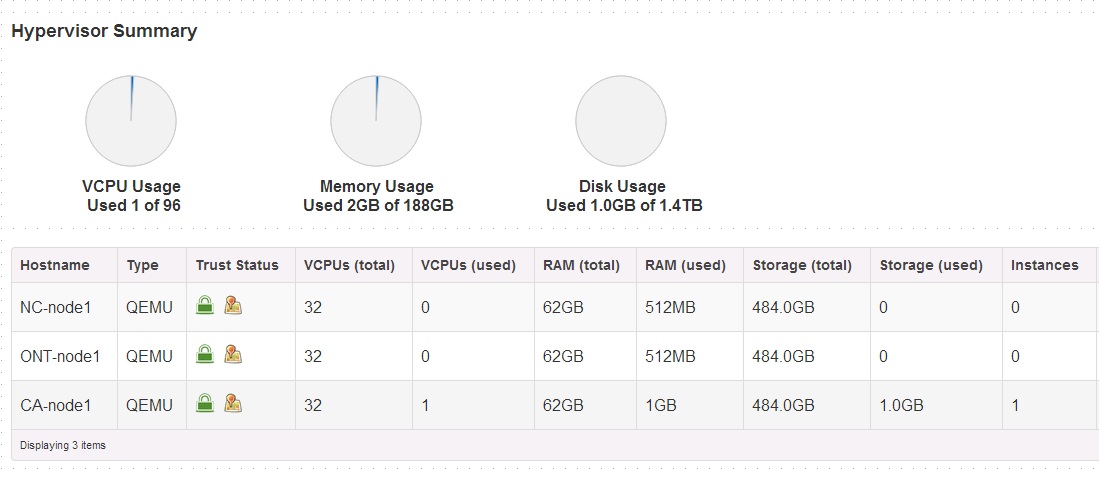
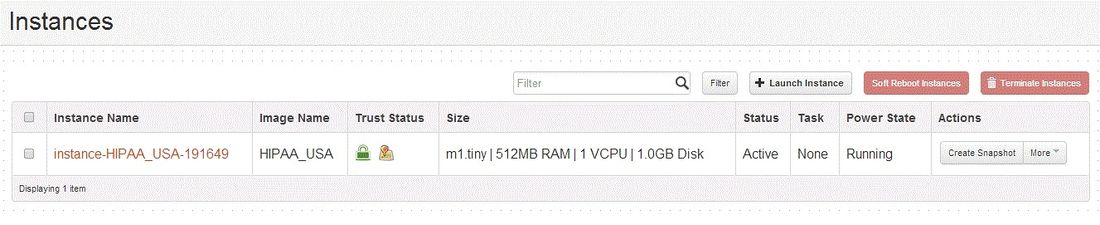
- Horizon dashboards have been updated to display Trust Status in 2 dashboards under the Admin Tab – Hypervisor and Instances
- The Hypervisor dashboard displays trust status of all Policies (Platform and Location). In addition, when you mouse over the location icon it will show the Asset/Geo tag provisioned in the Hardware of the host.
- Every time the Hypervisor dashboard is loaded, ‘Trust Status’ is updated by fetching the SAML assertion from the ‘Remote Attestation Service’ using Restful API.
- The Instance dashboard displays trust status of all Policies (Platform and Location). In addition, when you mouse over the location icon it will show the Location/ Tag Policy applied.
- if there are no Trust policies associated to the image the Instance is using, then the Trust Status for that instance will be empty.
- Trusted Icons for each policy will be displayed in ‘green’ and untrusted in ‘Red’
- Below are screen shots of the horizon hypervisor and instance dashboard.
Nova Aggregates and Availability Zones
The partitioning, resource reservation, and fault tolerance benefits, that Nova aggregates and availability zones bring, have a lot in common with geo/asset tags. However, the main difference is that trusted tags are provision time values, and attached to the hardware resource. The trusted geo/asset tag by virtue of being associated with a hardware root of trust is more valuable with respect to meeting regulatory requirements.
Nova Compute Node Provisioning
During compute nodes provisioning, geo/asset tags may also be assigned. These can be simple strings, such as, "3 rd Floor, Expo Center, Hong Kong", or complex, such as XML data providing sub-items such as GPS co-ordinates, postal address, and more, or json strings.
Nova Scheduler Filter
Asset /Geo Tag filters are specified. They will be very similar to today's Aggregate and Availability filters with the distinction that the data they retrieve from the Attestation service may need to be parsed. For instance, geo/asset tag is retrieved as XML.
Attestation Service
Existing Remote Attestation servers need to be upgraded to understand geo/asset tags, supporting the API to retrieve them for registered hardware resources. The geo/asset tags retrieved for hardware resource could be cached at the attestation service or even at the nova scheduler to speed scheduling decisions as long as the cached value is no older than some specifiable time window.