Security/Threat Analysis
Contents
OpenStack Threat Anlaysis
This proposal is to start a threat analysis evaluation of the OpenStack system components. A threat analysis takes a comprehensive look at the system at hand – components, protocols and code - against the existence and capability of an adversary looking for known vulnerabilities. When a threat is identified, it is tallied and reported to the development team. In some cases, the threat analysis team may also include a suggestion to fix the vulnerabilities and related threat.
Threat Analysis Steps
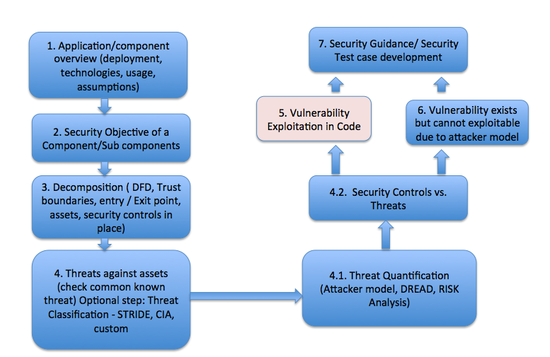
Threat Modelling Process for OpenStack Projects
File:Threat modeling process.pdf
Resources
On Going Work
Earlier we have used Google Docs for sharing documents, documents are still shared from Google Docs, but we are focusing to use GIT as a repository containing all docs.
Git Repo: https://github.com/shohel02/OpenStack_Threat_Modelling.git
Meeting
Meeting on IRC Channel every alternate Fridays's 17.00 UTC at Freenode's ##openstack-threat-analysis (unofficial channel),
- Threat Analysis Example
File:Threat analysis Example.pdf
- Keystone GAP and Threat Identification for Folsom Release (Quick Study)
File:OpenStack Keystone Analysis.pdf
Existing Literature Study
Process
- https://www.owasp.org/index.php/Threat_Risk_Modeling
- Michael Howard, David LeBlanc, Writing Secure Code, Second Edition, Microsoft Press
- Ross Anderson, Security Engineering, Chapter 11 http://www.cl.cam.ac.uk/~rja14/book.html
- The Notorious Nine, Cloud Security Alliance The_Notorious_Nine_Cloud_Computing_Top_Threats_in_2013.pdf
Identity and Access Management System Analysis
- Identity Management Protection Profile, http://www.commoncriteriaportal.org/files/ppfiles/pp0024b.pdf