Difference between revisions of "Security/Threat Analysis"
(→Threat Analysis Steps) |
|||
| Line 6: | Line 6: | ||
File:Modeling_steps.png | File:Modeling_steps.png | ||
</gallery> | </gallery> | ||
| + | |||
| + | === Existing Literature on Threat Analysis === | ||
| + | |||
| + | ==== Process ==== | ||
| + | 1. [https://www.owasp.org/index.php/Threat_Risk_Modeling%20 https://www.owasp.org/index.php/Threat_Risk_Modeling ] | ||
| + | 2. Michael Howard, David LeBlanc, Writing Secure Code, Second Edition, Microsoft Press | ||
| + | 3. Ross Anderson, Security Engineering, Chapter 11 http://www.cl.cam.ac.uk/~rja14/book.html | ||
| + | |||
| + | ==== Existing Threat Analysis Work related to Cloud ==== | ||
| + | 1. The Notorious Nine, Cloud Security Alliance [https://downloads.cloudsecurityalliance.org/initiatives/top_threats/The_Notorious_Nine_Cloud_Computing_Top_Threats_in_2013.pdf The_Notorious_Nine_Cloud_Computing_Top_Threats_in_2013.pdf] | ||
Revision as of 13:25, 13 November 2013
Contents
OpenStack Threat Anlaysis
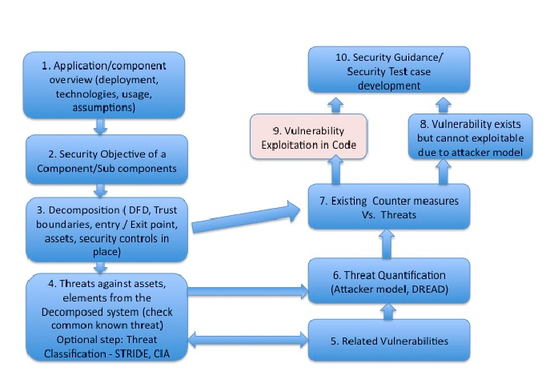
This proposal is to start a threat analysis evaluation of the OpenStack system components. A threat analysis takes a comprehensive look at the system at hand – components, protocols and code - against the existence and capability of an adversary looking for known vulnerabilities. When a threat is identified, it is tallied and reported to the development team. In some cases, the threat analysis team may also include a suggestion to fix the vulnerabilities and related threat.
Threat Analysis Steps
Existing Literature on Threat Analysis
Process
1. https://www.owasp.org/index.php/Threat_Risk_Modeling 2. Michael Howard, David LeBlanc, Writing Secure Code, Second Edition, Microsoft Press 3. Ross Anderson, Security Engineering, Chapter 11 http://www.cl.cam.ac.uk/~rja14/book.html
1. The Notorious Nine, Cloud Security Alliance The_Notorious_Nine_Cloud_Computing_Top_Threats_in_2013.pdf