Difference between revisions of "Security/Threat Analysis"
< Security
(→Threat Modelling Process for OpenStack Projects) |
|||
| Line 10: | Line 10: | ||
[[File:Threat_modeling_process.pdf|thumbnail|Threat Modelling Process]] | [[File:Threat_modeling_process.pdf|thumbnail|Threat Modelling Process]] | ||
| + | == Resources == | ||
| − | Threat Analysis Example | + | ==== On Going Work === |
| + | |||
| + | [https://drive.google.com/file/d/0B1aEVfmQtqnobzB6M21uMEFXNUE/edit?usp=sharing Keystone Threat Modelling] | ||
| + | |||
| + | ==== Meeting === | ||
| + | Meeting on IRC Channel on every alternate Fridays's 17.00 UTC | ||
| + | at Freenode's ##openstack-threat-analysis (unofficial channel) | ||
| + | More on meeting information | ||
| + | |||
| + | |||
| + | === Earlier reports on Threat Modelling related to OpenStack === | ||
| + | #Threat Analysis Example | ||
[[File:Threat analysis Example.pdf|thumbnail|Threat Analysis Example]] | [[File:Threat analysis Example.pdf|thumbnail|Threat Analysis Example]] | ||
| + | # Keystone GAP and Threat Identification for Folsom Release (Quick Study) | ||
| + | [[File:OpenStack Keystone Analysis.pdf|OpenStack Keystone GAP and Threat Identification]] | ||
| − | === Existing Literature | + | === Existing Literature Study === |
| − | |||
==== Process ==== | ==== Process ==== | ||
# [https://www.owasp.org/index.php/Threat_Risk_Modeling%20 https://www.owasp.org/index.php/Threat_Risk_Modeling ] | # [https://www.owasp.org/index.php/Threat_Risk_Modeling%20 https://www.owasp.org/index.php/Threat_Risk_Modeling ] | ||
| Line 26: | Line 39: | ||
==== Identity and Access Management System Analysis ==== | ==== Identity and Access Management System Analysis ==== | ||
# Identity Management Protection Profile, http://www.commoncriteriaportal.org/files/ppfiles/pp0024b.pdf | # Identity Management Protection Profile, http://www.commoncriteriaportal.org/files/ppfiles/pp0024b.pdf | ||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
Revision as of 12:46, 24 February 2014
Contents
OpenStack Threat Anlaysis
This proposal is to start a threat analysis evaluation of the OpenStack system components. A threat analysis takes a comprehensive look at the system at hand – components, protocols and code - against the existence and capability of an adversary looking for known vulnerabilities. When a threat is identified, it is tallied and reported to the development team. In some cases, the threat analysis team may also include a suggestion to fix the vulnerabilities and related threat.
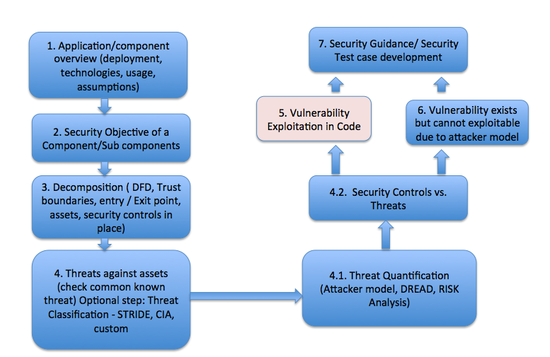
Threat Analysis Steps
Threat Modelling Process for OpenStack Projects
File:Threat modeling process.pdf
Resources
= On Going Work
= Meeting
Meeting on IRC Channel on every alternate Fridays's 17.00 UTC at Freenode's ##openstack-threat-analysis (unofficial channel) More on meeting information
- Threat Analysis Example
File:Threat analysis Example.pdf
- Keystone GAP and Threat Identification for Folsom Release (Quick Study)
File:OpenStack Keystone Analysis.pdf
Existing Literature Study
Process
- https://www.owasp.org/index.php/Threat_Risk_Modeling
- Michael Howard, David LeBlanc, Writing Secure Code, Second Edition, Microsoft Press
- Ross Anderson, Security Engineering, Chapter 11 http://www.cl.cam.ac.uk/~rja14/book.html
- The Notorious Nine, Cloud Security Alliance The_Notorious_Nine_Cloud_Computing_Top_Threats_in_2013.pdf
Identity and Access Management System Analysis
- Identity Management Protection Profile, http://www.commoncriteriaportal.org/files/ppfiles/pp0024b.pdf