Security-SIG
Security issues, tooling, innovations and education within OpenStack are the responsibility of the Security project. The Security project is a horizontal effort within OpenStack that is comprised of what was previously referred to as the OpenStack Security Group. The Vulnerability Management Team is also a part of the Security project. If you're looking to report a vulnerability then such discussions should be had directly with the VMT as per the links below.
Contents
How to contribute OpenStack Security
Go here: Lots of very good content! https://wiki.openstack.org/wiki/Security/How_To_Contribute
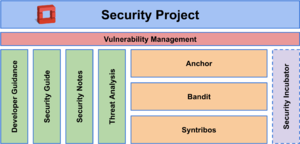
OpenStack Security Project Activities
The OpenStack Security Project has a number of ongoing activities that aim to enhance security of the OpenStack cloud ecosystem.
Vulnerability Management Team
The OpenStack Vulnerability Management team is the first point of contact for OpenStack security issues. They are responsible for the vulnerability handling and disclosure process.
See http://wiki.openstack.org/VulnerabilityManagement
OpenStack Security Guide
This book was written by a close community of security experts from the OpenStack Security Group in a short, intense week-long effort at an undisclosed location. One of the goals for this book is to bring together interested members to capture their collective knowledge and give it back to the OpenStack community.
See http://docs.openstack.org/sec/
Security Aware Development
Please use the resource below to help you develop more securely for OpenStack.
See https://github.com/openstack-security/Developer-Guidance
OpenStack Security Activities
The Security project exists to provide developers and consumers of OpenStack with appropriate security guidance and advice. To develop tooling that enhances levels of security within OpenStack projects. To issue Security Notes and Security Advisories for reported vulnerabilities and to foster new security initiatives to the benefit of the OpenStack community as a whole.
See https://launchpad.net/~openstack-ossg
Getting started
The process of becoming a member of the group is described on the OSSG Launchpad page. At the moment of writing, there is no defined "procedure" to get involved into the OSSG and a suggested set of steps follows. Each described steps might or not be relevant depending on the individual member's background and familiarity with the OpenStack project.
Some steps to get started are:
- Read the OpenStack documentation and understand the most common deployment scenarios.
- Go through the OpenStack installation guide and create a deployment (either a native one or in a virtualized environment), in order to get a basic understanding of the interaction of the different OpenStack services. Some installation scripts such as Devstack and Packstack are readily available. However, you should not underestimate the educational benefits of spending some quality time to install OpenStack manually.
- Read the newly released OpenStack security guide in order to dive into the security aspects of setting up and running an OpenStack deployment.
- Getting acquainted to some degree with the rest of the OpenStack manuals is highly encouraged.
- The next step is to choose one of the OpenStack components in order to become closely familiarized with it and eventually be able to use the combined expertise of the OSSG in order to make thoughtful contributions to the component (code reviews, direct code contribution, architectural aspects) and improve its security. It is of course important to chose a component that would closely match your interests; given the size of OpenStack, becoming closely familiar with the chosen component's code base, deployment and administration practices might require significant time investments. Once you have chosen a component, send an email on the OSSG email list to let others know about your intentions.
See https://wiki.openstack.org/wiki/Security/How_To_Contribute for more details on how you can improve OpenStack security.