Difference between revisions of "Quantum-generic-firewall"
Clark Boylan (talk | contribs) |
|||
| (10 intermediate revisions by one other user not shown) | |||
| Line 1: | Line 1: | ||
| − | |||
* '''Git Branch''': https://github.com/locaweb/quantum | * '''Git Branch''': https://github.com/locaweb/quantum | ||
= Handling layer 3 = | = Handling layer 3 = | ||
| − | + | __TOC__ | |
== Abstract == | == Abstract == | ||
| Line 11: | Line 10: | ||
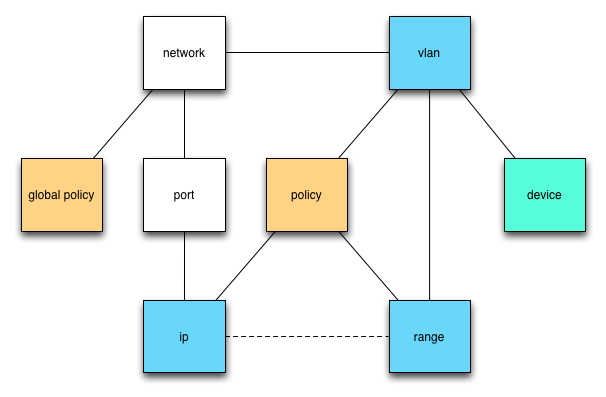
== Design == | == Design == | ||
| − | [[ | + | [[Image:quantum-generic-firewall-flow.jpg||alt L3 Firewalls Design]] |
== Summary == | == Summary == | ||
| Line 20: | Line 19: | ||
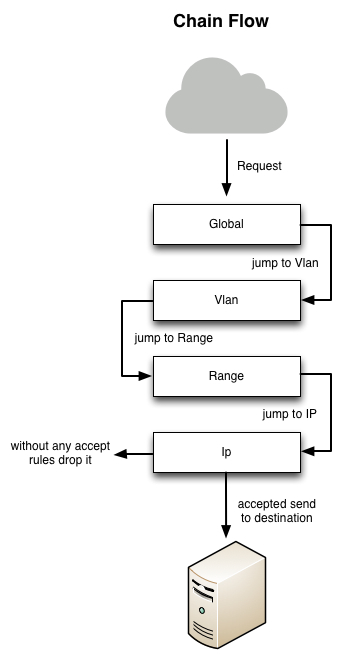
=== Firewall === | === Firewall === | ||
| − | Firewall agent | + | Firewall agent runs on top of linux firewall box, each ip has its own firewall policy for input and output traffic and you can also enforce a range or network policy to each one which will prevail over the bottom level policy, according to the follow hierarchy: network > vlan > range > ip |
| − | [[ | + | [[Image:quantum-generic-firewall.jpg||alt L3 Firewalls Workflow]] |
| + | |||
| + | ---- | ||
| + | |||
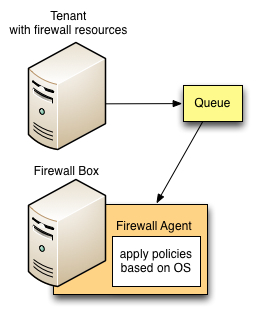
| + | [[Image:quantum-generic-firewall-agent.jpg||alt L3 Firewalls Agent]] | ||
= Proposed Quantum API Operations = | = Proposed Quantum API Operations = | ||
| Line 31: | Line 34: | ||
Creating a Policy should be done directly associated with the network entity. | Creating a Policy should be done directly associated with the network entity. | ||
| − | Quantum should handle which firewalls would process the policy, based on the provided dst | + | Quantum should handle which firewalls would process the policy, based on the provided dst, cidr or vlan. |
The default firewall policy we are working with is DROP, so the policies you should add are to ALLOW the packages. | The default firewall policy we are working with is DROP, so the policies you should add are to ALLOW the packages. | ||
| Line 38: | Line 41: | ||
POST /tenants/XYZ/networks/158233b0-ca9a-40b4-8614-54a4a99d47d1/policies.xml | POST /tenants/XYZ/networks/158233b0-ca9a-40b4-8614-54a4a99d47d1/policies.xml | ||
| − | < | + | <source lang="xml"> |
<policy> | <policy> | ||
<protocol>tcp</protocol> | <protocol>tcp</protocol> | ||
| Line 44: | Line 47: | ||
<dst_port>80</dst_port> | <dst_port>80</dst_port> | ||
</policy> | </policy> | ||
| − | </ | + | </source> |
| − | |||
Response: | Response: | ||
| − | < | + | <source lang="xml"> |
<policy> | <policy> | ||
<id>98017ddc-efc8-4c25-a915-774b2a633855<id/> | <id>98017ddc-efc8-4c25-a915-774b2a633855<id/> | ||
| Line 56: | Line 58: | ||
<dst_port>80</dst_port> | <dst_port>80</dst_port> | ||
</policy> | </policy> | ||
| − | </ | + | </source> |
| − | |||
'''List Policies''' | '''List Policies''' | ||
| Line 67: | Line 68: | ||
Response: | Response: | ||
| − | < | + | <source lang="xml"> |
<policies> | <policies> | ||
<!-- network policy --> | <!-- network policy --> | ||
| Line 81: | Line 82: | ||
<protocol>tcp</protocol> | <protocol>tcp</protocol> | ||
<src>0.0.0.0/0</src> | <src>0.0.0.0/0</src> | ||
| − | <dst> | + | <dst>vl-smtp-01</dst> |
<dst_port>8081</dst_port> | <dst_port>8081</dst_port> | ||
</policy> | </policy> | ||
| Line 101: | Line 102: | ||
</policy> | </policy> | ||
</policy> | </policy> | ||
| − | </ | + | </source> |
| − | |||
'''Delete Policy''' | '''Delete Policy''' | ||
| Line 109: | Line 109: | ||
DELETE /tenants/XYZ/networks/158233b0-ca9a-40b4-8614-54a4a99d47d1/policies/98017ddc-efc8-4c25-a915-774b2a633855.xml | DELETE /tenants/XYZ/networks/158233b0-ca9a-40b4-8614-54a4a99d47d1/policies/98017ddc-efc8-4c25-a915-774b2a633855.xml | ||
| + | |||
| + | == Devices == | ||
| + | |||
| + | Describes Devices associated with a network. | ||
| + | |||
| + | '''Create Devices/Associate with a network''' | ||
| + | |||
| + | POST /tenants/XYZ/networks/158233b0-ca9a-40b4-8614-54a4a99d47d1/device.xml | ||
| + | |||
| + | <source lang="xml"> | ||
| + | <vlan> | ||
| + | <name>firewall-01</name> | ||
| + | </vlan> | ||
| + | </source> | ||
== Vlans == | == Vlans == | ||
| Line 114: | Line 128: | ||
Describes Vlans associated with a network. | Describes Vlans associated with a network. | ||
| − | ''Create Vlan/Associate with a network''' | + | '''Create Vlan/Associate with a network''' |
POST /tenants/XYZ/networks/158233b0-ca9a-40b4-8614-54a4a99d47d1/vlan.xml | POST /tenants/XYZ/networks/158233b0-ca9a-40b4-8614-54a4a99d47d1/vlan.xml | ||
| − | < | + | <source lang="xml"> |
<vlan> | <vlan> | ||
<name>vl-smtp-01</name> | <name>vl-smtp-01</name> | ||
</vlan> | </vlan> | ||
| − | </ | + | </source> |
| + | '''Attach a Vlan to device''' | ||
| + | |||
| + | POST /tenants/XYZ/networks/158233b0-ca9a-40b4-8614-54a4a99d47d1/device/98017ddc-efc8-4c25-a915-774b2a633859/ranges.xml | ||
| + | |||
| + | <source lang="xml"> | ||
| + | <vlan> | ||
| + | <name>vl-smtp-01</name> | ||
| + | </vlan> | ||
| + | </source> | ||
== Ranges == | == Ranges == | ||
| Line 134: | Line 157: | ||
POST /tenants/XYZ/networks/158233b0-ca9a-40b4-8614-54a4a99d47d1/vlan/98017ddc-efc8-4c25-a915-774b2a633858/ranges.xml | POST /tenants/XYZ/networks/158233b0-ca9a-40b4-8614-54a4a99d47d1/vlan/98017ddc-efc8-4c25-a915-774b2a633858/ranges.xml | ||
| − | < | + | <source lang="xml"> |
<ip_range> | <ip_range> | ||
<address>192.168.0.0/24</address> | <address>192.168.0.0/24</address> | ||
</ip_range> | </ip_range> | ||
| − | </ | + | </source> |
| − | |||
== IPs == | == IPs == | ||
| Line 150: | Line 172: | ||
POST /tenants/XYZ/networks/158233b0-ca9a-40b4-8614-54a4a99d47d1/ports/98017ddc-efc8-4c25-a915-774b2a633855/ips.xml | POST /tenants/XYZ/networks/158233b0-ca9a-40b4-8614-54a4a99d47d1/ports/98017ddc-efc8-4c25-a915-774b2a633855/ips.xml | ||
| − | < | + | <source lang="xml"> |
<ip> | <ip> | ||
<address>192.168.0.3</address> | <address>192.168.0.3</address> | ||
</ip> | </ip> | ||
| − | </ | + | </source> |
| − | |||
| − | (Contact: Willian Molinari ([[PotHix]]), Thiago Morello, Juliano Martinez(ncode)) | + | (Contact: Willian Molinari ([[PotHix]]), Thiago Morello, Juliano Martinez (ncode)) |
Latest revision as of 22:29, 16 February 2013
- Git Branch: https://github.com/locaweb/quantum
Handling layer 3
Contents
Abstract
The idea behind this blueprint is to extend quantum to provide a generic interface to control datacenter firewalls
Design
Summary
Agents are running on firewalls to execute the proper work dictated by quantum via amqp: The firewall plugin is currently working with linux, but the data model should be usable with any firewall regarding the agent development
Firewall
Firewall agent runs on top of linux firewall box, each ip has its own firewall policy for input and output traffic and you can also enforce a range or network policy to each one which will prevail over the bottom level policy, according to the follow hierarchy: network > vlan > range > ip
Proposed Quantum API Operations
Policies
Create Policy
Creating a Policy should be done directly associated with the network entity. Quantum should handle which firewalls would process the policy, based on the provided dst, cidr or vlan. The default firewall policy we are working with is DROP, so the policies you should add are to ALLOW the packages.
Request:
POST /tenants/XYZ/networks/158233b0-ca9a-40b4-8614-54a4a99d47d1/policies.xml
<policy>
<protocol>tcp</protocol>
<src>0.0.0.0/0</src>
<dst_port>80</dst_port>
</policy>
Response:
<policy>
<id>98017ddc-efc8-4c25-a915-774b2a633855<id/>
<protocol>tcp</protocol>
<src>0.0.0.0/0</src>
<dst_port>80</dst_port>
</policy>
List Policies
Request:
GET /tenants/XYZ/networks/158233b0-ca9a-40b4-8614-54a4a99d47d1/policies.xml
Response:
<policies>
<!-- network policy -->
<policy>
<id>98017ddc-efc8-4c25-a915-774b2a633855<id/>
<protocol>tcp</protocol>
<src>0.0.0.0/0</src>
<dst_port>80</dst_port>
</policy>
<!-- vlan policy -->
<policy>
<id>98017ddc-efc8-4c25-a915-774b2a633858<id/>
<protocol>tcp</protocol>
<src>0.0.0.0/0</src>
<dst>vl-smtp-01</dst>
<dst_port>8081</dst_port>
</policy>
<!-- range policy -->
<policy>
<id>98017ddc-efc8-4c25-a915-774b2a633856<id/>
<protocol>tcp</protocol>
<src>0.0.0.0/0</src>
<dst>192.168.1.0/24</dst>
<dst_port>8080</dst_port>
</policy>
<!-- ip policy -->
<policy>
<id>98017ddc-efc8-4c25-a915-774b2a633857<id/>
<protocol>tcp</protocol>
<src>0.0.0.0/0</src>
<dst>192.168.1.3</dst>
<dst_port>8000</dst_port>
</policy>
</policy>
Delete Policy
Request:
DELETE /tenants/XYZ/networks/158233b0-ca9a-40b4-8614-54a4a99d47d1/policies/98017ddc-efc8-4c25-a915-774b2a633855.xml
Devices
Describes Devices associated with a network.
Create Devices/Associate with a network
POST /tenants/XYZ/networks/158233b0-ca9a-40b4-8614-54a4a99d47d1/device.xml
<vlan>
<name>firewall-01</name>
</vlan>
Vlans
Describes Vlans associated with a network.
Create Vlan/Associate with a network
POST /tenants/XYZ/networks/158233b0-ca9a-40b4-8614-54a4a99d47d1/vlan.xml
<vlan>
<name>vl-smtp-01</name>
</vlan>
Attach a Vlan to device
POST /tenants/XYZ/networks/158233b0-ca9a-40b4-8614-54a4a99d47d1/device/98017ddc-efc8-4c25-a915-774b2a633859/ranges.xml
<vlan>
<name>vl-smtp-01</name>
</vlan>
Ranges
Describes IP ranges associated with a vlan. Quantum should validade if the range isn't conflicting with any range associated with the vlan.
Create Range/Associate with a vlan
POST /tenants/XYZ/networks/158233b0-ca9a-40b4-8614-54a4a99d47d1/vlan/98017ddc-efc8-4c25-a915-774b2a633858/ranges.xml
<ip_range>
<address>192.168.0.0/24</address>
</ip_range>
IPs
Describes which IPs are allowed in a network's port. Quantum should validade if the network is compatible with a range that may contain the IP.
Create IP
POST /tenants/XYZ/networks/158233b0-ca9a-40b4-8614-54a4a99d47d1/ports/98017ddc-efc8-4c25-a915-774b2a633855/ips.xml
<ip>
<address>192.168.0.3</address>
</ip>
(Contact: Willian Molinari (PotHix), Thiago Morello, Juliano Martinez (ncode))