|
|
| (5 intermediate revisions by 3 users not shown) |
| Line 1: |
Line 1: |
| − | == Installation == | + | == Trying out FWaaS using Devstack== |
| | | | |
| − | | + | Add these lines in localrc: |
| − | == Checkout Test branches ==
| |
| − | | |
| − | * Horizon: https://review.openstack.org/#/c/38724/
| |
| − | | |
| − | Please add this line on localrc
| |
| | | | |
| | enable_service q-fwaas | | enable_service q-fwaas |
| | | | |
| − | == Setup Params ==
| |
| − |
| |
| − | * If you used the devstack patch above, you can skip this section
| |
| − |
| |
| − | * If you did not use the devstack patch above and installed devstack from the trunk, after the installation add the following to
| |
| − |
| |
| − | /etc/neutron/neutron.conf
| |
| − |
| |
| − | <pre><nowiki>
| |
| − | service_plugins = neutron.services.firewall.fwaas_plugin.FirewallPlugin
| |
| − | </nowiki></pre>
| |
| − |
| |
| − | Note: you can also add this line on localrc (before running stack.sh to get the above configuration automatically)
| |
| | | | |
| | Q_SERVICE_PLUGIN_CLASSES=neutron.services.firewall.fwaas_plugin.FirewallPlugin | | Q_SERVICE_PLUGIN_CLASSES=neutron.services.firewall.fwaas_plugin.FirewallPlugin |
| | | | |
| | | | |
| − | * Add the following file: | + | * The following will be populated by after the devstack installation: |
| | | | |
| − | /etc/neutron/fwaas_driver.ini | + | /etc/neutron/l3_agent.ini |
| | | | |
| | <pre><nowiki> | | <pre><nowiki> |
| | [fwaas] | | [fwaas] |
| − | driver = neutron.services.firewall.drivers.linux.iptables_fwaas.IptablesFwaasDriver | + | driver = neutron_fwaas.services.firewall.drivers.linux.iptables_fwaas.IptablesFwaasDriver |
| | enabled = True | | enabled = True |
| | </nowiki></pre> | | </nowiki></pre> |
| − |
| |
| − | * Restart the l3 agent
| |
| − | When you do this, you will need to provide the fwaas_driver.ini conf file as an argument as well:
| |
| − |
| |
| − | <pre><nowiki>
| |
| − | cd /opt/stack/neutron && python /usr/local/bin/neutron-l3-agent --config-file /etc/neutron/neutron.conf --config-file /etc/neutron/plugins/openvswitch/ovs_neutron_plugin.ini --config-file /etc/neutron/fwaas_driver.ini || touch "/opt/stack/status/stack/q-agt.failure"
| |
| − | </nowiki></pre>
| |
| − |
| |
| − | * Restart the neutron server
| |
| | | | |
| | == CLI/REST Walkthrough == | | == CLI/REST Walkthrough == |
| Line 190: |
Line 163: |
| | | | |
| | curl -X DELETE -H "X-Auth-Token: $auth_token" $q_url/fw/firewalls/9649548e-b87f-4c56-bbb7-5ee84b316da1 | | curl -X DELETE -H "X-Auth-Token: $auth_token" $q_url/fw/firewalls/9649548e-b87f-4c56-bbb7-5ee84b316da1 |
| − |
| |
| − | == FWaaS and VPNaaS Integration Tests ==
| |
| − | === Objective ===
| |
| − | Validate basic functionality with FWaaS and VPNaaS enabled.
| |
| − |
| |
| − | 1) Set up a VPN tunnel between devstack instance East and devstack instance West - validate connectivity.
| |
| − |
| |
| − | 2) Apply firewall rules and verify that the behavior is as expected.
| |
| − |
| |
| − | === Setup VPN tunnel across 2 devstack instances (East & West) ===
| |
| − | Add
| |
| − |
| |
| − | enable_service q-fwaas
| |
| − |
| |
| − | enable_service q-vpn
| |
| − |
| |
| − | to localrc
| |
| − |
| |
| − | Use directions from:
| |
| − | https://wiki.openstack.org/wiki/Quantum/VPNaaS/HowToInstall
| |
| − |
| |
| − | for VPN setup. Firewall setup directions are present on this wiki page.
| |
| − |
| |
| − | ==== Verify Tunnel ====
| |
| − | neutron ipsec-site-connection-show vpnconnection1
| |
| − |
| |
| − | East:
| |
| − | <pre><nowiki>
| |
| − | stack@east-virtual-machine:~/devstack$ neutron ipsec-site-connection-show vpnconnection1
| |
| − | +----------------+----------------------------------------------------+
| |
| − | | Field | Value |
| |
| − | +----------------+----------------------------------------------------+
| |
| − | | admin_state_up | True |
| |
| − | | auth_mode | psk |
| |
| − | | description | |
| |
| − | | dpd | {"action": "hold", "interval": 30, "timeout": 120} |
| |
| − | | id | 8d2faebb-3b9c-4b93-8594-f2246c9a92ad |
| |
| − | | ikepolicy_id | eeeea7ad-d730-40b5-a24a-ecfa58113b53 |
| |
| − | | initiator | bi-directional |
| |
| − | | ipsecpolicy_id | 90597431-ee8f-46d2-a9f7-039efca0bed7 |
| |
| − | | mtu | 1500 |
| |
| − | | name | vpnconnection1 |
| |
| − | | peer_address | 172.24.4.21 |
| |
| − | | peer_cidrs | 10.2.0.0/24 |
| |
| − | | peer_id | 172.24.4.21 |
| |
| − | | psk | secret |
| |
| − | | route_mode | static |
| |
| − | | status | ACTIVE |
| |
| − | | tenant_id | d98aa7dd12f94af29a4c1d7b8174643c |
| |
| − | | vpnservice_id | 3f21d590-1e30-4d08-a412-a7d9e5b2560f |
| |
| − | +----------------+----------------------------------------------------+
| |
| − | stack@east-virtual-machine:~/devstack$
| |
| − | </nowiki></pre>
| |
| − |
| |
| − | West
| |
| − | <pre><nowiki>
| |
| − | stack@west:~/devstack$ neutron ipsec-site-connection-show vpnconnection1
| |
| − | +----------------+----------------------------------------------------+
| |
| − | | Field | Value |
| |
| − | +----------------+----------------------------------------------------+
| |
| − | | admin_state_up | True |
| |
| − | | auth_mode | psk |
| |
| − | | description | |
| |
| − | | dpd | {"action": "hold", "interval": 30, "timeout": 120} |
| |
| − | | id | b7330d13-0ff1-4529-b0d5-91c2e7c4cfbf |
| |
| − | | ikepolicy_id | 858eb8f5-a2ee-4649-861a-0f0ca5814556 |
| |
| − | | initiator | bi-directional |
| |
| − | | ipsecpolicy_id | ba86e218-6ef6-46a5-baf1-f63177590a6e |
| |
| − | | mtu | 1500 |
| |
| − | | name | vpnconnection1 |
| |
| − | | peer_address | 172.24.4.11 |
| |
| − | | peer_cidrs | 10.1.0.0/24 |
| |
| − | | peer_id | 172.24.4.11 |
| |
| − | | psk | secret |
| |
| − | | route_mode | static |
| |
| − | | status | ACTIVE |
| |
| − | | tenant_id | b0caec5cacce45babb19be70066b22ce |
| |
| − | | vpnservice_id | 9c6fee8a-85aa-4f8e-911e-95d4d5c997d7 |
| |
| − | +----------------+----------------------------------------------------+
| |
| − | stack@west:~/devstack$
| |
| − | </nowiki></pre>
| |
| − | Spawn the VMs
| |
| − |
| |
| − | East
| |
| − | <pre><nowiki>
| |
| − | stack@east-virtual-machine:~/devstack$ nova list
| |
| − | +--------------------------------------+----------+--------+------------+-------------+------------------+
| |
| − | | ID | Name | Status | Task State | Power State | Networks |
| |
| − | +--------------------------------------+----------+--------+------------+-------------+------------------+
| |
| − | | 23850324-d8d8-4859-a5ac-e48c2834e661 | East-VM1 | ACTIVE | None | Running | private=10.1.0.2 |
| |
| − | +--------------------------------------+----------+--------+------------+-------------+------------------+
| |
| − | </nowiki></pre>
| |
| − | West
| |
| − | <pre><nowiki>
| |
| − | stack@west:~/devstack$ nova list
| |
| − | +--------------------------------------+----------+--------+------------+-------------+------------------+
| |
| − | | ID | Name | Status | Task State | Power State | Networks |
| |
| − | +--------------------------------------+----------+--------+------------+-------------+------------------+
| |
| − | | c0cd320e-eab9-4131-b959-823f90bb7563 | West-VM1 | ACTIVE | None | Running | private=10.2.0.2 |
| |
| − | | e4e68302-d76b-4067-bce1-31e7634451d2 | West-VM2 | ACTIVE | None | Running | private=10.2.0.4 |
| |
| − | +--------------------------------------+----------+--------+------------+-------------+------------------+
| |
| − | stack@west:~/devstack$
| |
| − | </nowiki></pre>
| |
| − | Pings over VPN (no FW yet)
| |
| − |
| |
| − | East to West
| |
| − | <pre><nowiki>
| |
| − | sudo ip netns exec qrouter-2269732f-1e8d-42bb-bed4-7a1f7e101967 ssh cirros@10.1.0.2
| |
| − | The authenticity of host '10.1.0.2 (10.1.0.2)' can't be established.
| |
| − | RSA key fingerprint is 6b:1b:a8:e4:3a:d0:09:63:8d:7b:af:19:2b:e5:29:27.
| |
| − | Are you sure you want to continue connecting (yes/no)? yes
| |
| − | Warning: Permanently added '10.1.0.2' (RSA) to the list of known hosts.
| |
| − | cirros@10.1.0.2's password:
| |
| − |
| |
| − | $ ifconfig
| |
| − | eth0 Link encap:Ethernet HWaddr FA:16:3E:EC:DC:4B
| |
| − | inet addr:10.1.0.2 Bcast:10.1.0.255 Mask:255.255.255.0
| |
| − | inet6 addr: fe80::f816:3eff:feec:dc4b/64 Scope:Link
| |
| − | UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
| |
| − | RX packets:123 errors:0 dropped:0 overruns:0 frame:0
| |
| − | TX packets:80 errors:0 dropped:0 overruns:0 carrier:0
| |
| − | collisions:0 txqueuelen:1000
| |
| − | RX bytes:17909 (17.4 KiB) TX bytes:10258 (10.0 KiB)
| |
| − |
| |
| − | lo Link encap:Local Loopback
| |
| − | inet addr:127.0.0.1 Mask:255.0.0.0
| |
| − | inet6 addr: ::1/128 Scope:Host
| |
| − | UP LOOPBACK RUNNING MTU:16436 Metric:1
| |
| − | RX packets:0 errors:0 dropped:0 overruns:0 frame:0
| |
| − | TX packets:0 errors:0 dropped:0 overruns:0 carrier:0
| |
| − | collisions:0 txqueuelen:0
| |
| − | RX bytes:0 (0.0 B) TX bytes:0 (0.0 B)
| |
| − |
| |
| − | $ ping 10.2.0.2
| |
| − | PING 10.2.0.2 (10.2.0.2): 56 data bytes
| |
| − | 64 bytes from 10.2.0.2: seq=0 ttl=62 time=13.522 ms
| |
| − | 64 bytes from 10.2.0.2: seq=1 ttl=62 time=1.541 ms
| |
| − | ^C
| |
| − |
| |
| − | $ ping 10.2.0.4
| |
| − | PING 10.2.0.4 (10.2.0.4): 56 data bytes
| |
| − | 64 bytes from 10.2.0.4: seq=0 ttl=62 time=24.885 ms
| |
| − | 64 bytes from 10.2.0.4: seq=1 ttl=62 time=1.456 ms
| |
| − | 64 bytes from 10.2.0.4: seq=2 ttl=62 time=1.457 ms
| |
| − | ^C
| |
| − | </nowiki></pre>
| |
| − |
| |
| − | West to East
| |
| − | <pre><nowiki>
| |
| − | stack@west:~/devstack$ sudo ip netns exec qrouter-47e92836-08d8-4bb1-a2e9-6ac4eaec7610 ssh cirros@10.2.0.2
| |
| − | The authenticity of host '10.2.0.2 (10.2.0.2)' can't be established.
| |
| − | RSA key fingerprint is a0:0c:fb:f0:28:21:20:d2:27:39:9c:93:e9:77:36:ef.
| |
| − | Are you sure you want to continue connecting (yes/no)? yes
| |
| − | Warning: Permanently added '10.2.0.2' (RSA) to the list of known hosts.
| |
| − | cirros@10.2.0.2's password:
| |
| − | $ ifconfig
| |
| − | eth0 Link encap:Ethernet HWaddr FA:16:3E:10:ED:05
| |
| − | inet addr:10.2.0.2 Bcast:10.2.0.255 Mask:255.255.255.0
| |
| − | inet6 addr: fe80::f816:3eff:fe10:ed05/64 Scope:Link
| |
| − | UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
| |
| − | RX packets:77 errors:0 dropped:0 overruns:0 frame:0
| |
| − | TX packets:59 errors:0 dropped:0 overruns:0 carrier:0
| |
| − | collisions:0 txqueuelen:1000
| |
| − | RX bytes:10792 (10.5 KiB) TX bytes:7424 (7.2 KiB)
| |
| − |
| |
| − | lo Link encap:Local Loopback
| |
| − | inet addr:127.0.0.1 Mask:255.0.0.0
| |
| − | inet6 addr: ::1/128 Scope:Host
| |
| − | UP LOOPBACK RUNNING MTU:16436 Metric:1
| |
| − | RX packets:0 errors:0 dropped:0 overruns:0 frame:0
| |
| − | TX packets:0 errors:0 dropped:0 overruns:0 carrier:0
| |
| − | collisions:0 txqueuelen:0
| |
| − | RX bytes:0 (0.0 B) TX bytes:0 (0.0 B)
| |
| − |
| |
| − | $ ping 10.1.0.2
| |
| − | PING 10.1.0.2 (10.1.0.2): 56 data bytes
| |
| − | 64 bytes from 10.1.0.2: seq=0 ttl=62 time=21.485 ms
| |
| − | 64 bytes from 10.1.0.2: seq=1 ttl=62 time=1.332 ms
| |
| − | 64 bytes from 10.1.0.2: seq=2 ttl=62 time=1.477 ms
| |
| − | ^C
| |
| − | --- 10.1.0.2 ping statistics ---
| |
| − | 3 packets transmitted, 3 packets received, 0% packet loss
| |
| − | round-trip min/avg/max = 1.332/8.098/21.485 ms
| |
| − | $
| |
| − | </nowiki></pre>
| |
| − |
| |
| − | === Add a Firewall with a rule to deny all icmp on West ===
| |
| − |
| |
| − | <pre><nowiki>
| |
| − | stack@west:~/devstack$ neutron firewall-rule-create --protocol icmp --action deny
| |
| − | Created a new firewall_rule:
| |
| − | +------------------------+--------------------------------------+
| |
| − | | Field | Value |
| |
| − | +------------------------+--------------------------------------+
| |
| − | | action | deny |
| |
| − | | description | |
| |
| − | | destination_ip_address | |
| |
| − | | destination_port | |
| |
| − | | enabled | True |
| |
| − | | firewall_policy_id | |
| |
| − | | id | f1deebab-5a54-4a98-8684-174e967c5520 |
| |
| − | | ip_version | 4 |
| |
| − | | name | |
| |
| − | | position | |
| |
| − | | protocol | icmp |
| |
| − | | shared | False |
| |
| − | | source_ip_address | |
| |
| − | | source_port | |
| |
| − | | tenant_id | b0caec5cacce45babb19be70066b22ce |
| |
| − | +------------------------+--------------------------------------+
| |
| − | stack@west:~/devstack$ neutron firewall-policy-create --firewall-rules "f1deebab-5a54-4a98-8684-174e967c5520" test-policy
| |
| − | Created a new firewall_policy:
| |
| − | +----------------+--------------------------------------+
| |
| − | | Field | Value |
| |
| − | +----------------+--------------------------------------+
| |
| − | | audited | False |
| |
| − | | description | |
| |
| − | | firewall_rules | f1deebab-5a54-4a98-8684-174e967c5520 |
| |
| − | | id | cff10b50-a324-4640-9cf8-a88538c429ef |
| |
| − | | name | test-policy |
| |
| − | | shared | False |
| |
| − | | tenant_id | b0caec5cacce45babb19be70066b22ce |
| |
| − | +----------------+--------------------------------------+
| |
| − | stack@west:~/devstack$ neutron firewall-create cff10b50-a324-4640-9cf8-a88538c429ef
| |
| − | Created a new firewall:
| |
| − | +--------------------+--------------------------------------+
| |
| − | | Field | Value |
| |
| − | +--------------------+--------------------------------------+
| |
| − | | admin_state_up | True |
| |
| − | | description | |
| |
| − | | firewall_policy_id | cff10b50-a324-4640-9cf8-a88538c429ef |
| |
| − | | id | 3772cc7a-3467-4238-82b8-904d50ebfb4d |
| |
| − | | name | |
| |
| − | | status | PENDING_CREATE |
| |
| − | | tenant_id | b0caec5cacce45babb19be70066b22ce |
| |
| − | +--------------------+--------------------------------------+
| |
| − | stack@west:~/devstack$ neutron firewall-show 3772cc7a-3467-4238-82b8-904d50ebfb4d
| |
| − | +--------------------+--------------------------------------+
| |
| − | | Field | Value |
| |
| − | +--------------------+--------------------------------------+
| |
| − | | admin_state_up | True |
| |
| − | | description | |
| |
| − | | firewall_policy_id | cff10b50-a324-4640-9cf8-a88538c429ef |
| |
| − | | id | 3772cc7a-3467-4238-82b8-904d50ebfb4d |
| |
| − | | name | |
| |
| − | | status | ACTIVE |
| |
| − | | tenant_id | b0caec5cacce45babb19be70066b22ce |
| |
| − | +--------------------+--------------------------------------+
| |
| − | stack@west:~/devstack$
| |
| − | </nowiki></pre>
| |
| − |
| |
| − | Ping from East to West
| |
| − |
| |
| − | <pre><nowiki>
| |
| − | $ ping 10.2.0.4
| |
| − | PING 10.2.0.4 (10.2.0.4): 56 data bytes
| |
| − | ^C
| |
| − | --- 10.2.0.4 ping statistics ---
| |
| − | 3 packets transmitted, 0 packets received, 100% packet loss
| |
| − | $ ping 10.2.0.2
| |
| − | PING 10.2.0.2 (10.2.0.2): 56 data bytes
| |
| − | ^C
| |
| − | --- 10.2.0.2 ping statistics ---
| |
| − | 4 packets transmitted, 0 packets received, 100% packet loss
| |
| − | $
| |
| − | </nowiki></pre>
| |
| − |
| |
| − | Ping from West to East
| |
| − | <pre><nowiki>
| |
| − | $ ifconfig
| |
| − | eth0 Link encap:Ethernet HWaddr FA:16:3E:10:ED:05
| |
| − | inet addr:10.2.0.2 Bcast:10.2.0.255 Mask:255.255.255.0
| |
| − | inet6 addr: fe80::f816:3eff:fe10:ed05/64 Scope:Link
| |
| − | UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
| |
| − | RX packets:230 errors:0 dropped:0 overruns:0 frame:0
| |
| − | TX packets:163 errors:0 dropped:0 overruns:0 carrier:0
| |
| − | collisions:0 txqueuelen:1000
| |
| − | RX bytes:25915 (25.3 KiB) TX bytes:20690 (20.2 KiB)
| |
| − |
| |
| − | lo Link encap:Local Loopback
| |
| − | inet addr:127.0.0.1 Mask:255.0.0.0
| |
| − | inet6 addr: ::1/128 Scope:Host
| |
| − | UP LOOPBACK RUNNING MTU:16436 Metric:1
| |
| − | RX packets:0 errors:0 dropped:0 overruns:0 frame:0
| |
| − | TX packets:0 errors:0 dropped:0 overruns:0 carrier:0
| |
| − | collisions:0 txqueuelen:0
| |
| − | RX bytes:0 (0.0 B) TX bytes:0 (0.0 B)
| |
| − |
| |
| − | $ ping 10.1.0.2
| |
| − | PING 10.1.0.2 (10.1.0.2): 56 data bytes
| |
| − | ^C
| |
| − | --- 10.1.0.2 ping statistics ---
| |
| − | 3 packets transmitted, 0 packets received, 100% packet loss
| |
| − | $
| |
| − | </nowiki></pre>
| |
| − |
| |
| − | Remove Firewall in West
| |
| − | <pre><nowiki>
| |
| − | stack@west:~/devstack$ neutron firewall-list
| |
| − | +--------------------------------------+------+--------------------------------------+
| |
| − | | id | name | firewall_policy_id |
| |
| − | +--------------------------------------+------+--------------------------------------+
| |
| − | | 3772cc7a-3467-4238-82b8-904d50ebfb4d | | cff10b50-a324-4640-9cf8-a88538c429ef |
| |
| − | +--------------------------------------+------+--------------------------------------+
| |
| − | stack@west:~/devstack$ neutron firewall-delete 3772cc7a-3467-4238-82b8-904d50ebfb4d
| |
| − | Deleted firewall: 3772cc7a-3467-4238-82b8-904d50ebfb4d
| |
| − | stack@west:~/devstack$ neutron firewall-list
| |
| − |
| |
| − | stack@west:~/devstack$
| |
| − | </nowiki></pre>
| |
| − |
| |
| − | Check Ping
| |
| − | <pre><nowiki>
| |
| − | $ ping 10.2.0.2
| |
| − | PING 10.2.0.2 (10.2.0.2): 56 data bytes
| |
| − | 64 bytes from 10.2.0.2: seq=0 ttl=62 time=14.469 ms
| |
| − | 64 bytes from 10.2.0.2: seq=1 ttl=62 time=1.458 ms
| |
| − | ^C
| |
| − | --- 10.2.0.2 ping statistics ---
| |
| − | 2 packets transmitted, 2 packets received, 0% packet loss
| |
| − | round-trip min/avg/max = 1.458/7.963/14.469 ms
| |
| − | $ ping 10.2.0.4
| |
| − | PING 10.2.0.4 (10.2.0.4): 56 data bytes
| |
| − | 64 bytes from 10.2.0.4: seq=0 ttl=62 time=13.530 ms
| |
| − | 64 bytes from 10.2.0.4: seq=1 ttl=62 time=1.732 ms
| |
| − | ^C
| |
| − | --- 10.2.0.4 ping statistics ---
| |
| − | 2 packets transmitted, 2 packets received, 0% packet loss
| |
| − | round-trip min/avg/max = 1.732/7.631/13.530 ms
| |
| − | </nowiki></pre>
| |
| − |
| |
| − | === Add a firewall with a destination icmp rule on East to allow pings to West-VM2 but not West-VM1 ===
| |
| − | <pre><nowiki>
| |
| − | stack@east-virtual-machine:~/devstack$ neutron firewall-rule-create --protocol icmp --destination_ip_address 10.2.0.4 --action allow
| |
| − | Created a new firewall_rule:
| |
| − | +------------------------+--------------------------------------+
| |
| − | | Field | Value |
| |
| − | +------------------------+--------------------------------------+
| |
| − | | action | allow |
| |
| − | | description | |
| |
| − | | destination_ip_address | 10.2.0.4 |
| |
| − | | destination_port | |
| |
| − | | enabled | True |
| |
| − | | firewall_policy_id | |
| |
| − | | id | a70cf19e-8178-4de6-85e3-6e2610fcc620 |
| |
| − | | ip_version | 4 |
| |
| − | | name | |
| |
| − | | position | |
| |
| − | | protocol | icmp |
| |
| − | | shared | False |
| |
| − | | source_ip_address | |
| |
| − | | source_port | |
| |
| − | | tenant_id | d98aa7dd12f94af29a4c1d7b8174643c |
| |
| − | +------------------------+--------------------------------------+
| |
| − | stack@east-virtual-machine:~/devstack$ neutron firewall-rule-list
| |
| − | +--------------------------------------+------+--------------------+------------------------+---------+
| |
| − | | id | name | firewall_policy_id | summary | enabled |
| |
| − | +--------------------------------------+------+--------------------+------------------------+---------+
| |
| − | | a70cf19e-8178-4de6-85e3-6e2610fcc620 | | | ICMP, | True |
| |
| − | | | | | source: none(none), | |
| |
| − | | | | | dest: 10.2.0.4(none), | |
| |
| − | | | | | allow | |
| |
| − | | f2349c92-3f1b-4aad-90ed-d6626b80f41e | | | ICMP, | True |
| |
| − | | | | | source: none(none), | |
| |
| − | | | | | dest: 10.2.0.2(none), | |
| |
| − | | | | | deny | |
| |
| − | +--------------------------------------+------+--------------------+------------------------+---------+
| |
| − | stack@east-virtual-machine:~/devstack$ neutron firewall-policy-create --firewall-rules "a70cf19e-8178-4de6-85e3-6e2610fcc620 f2349c92-3f1b-4aad-90ed-d6626b80f41e" test-policy-east
| |
| − | Created a new firewall_policy:
| |
| − | +----------------+--------------------------------------+
| |
| − | | Field | Value |
| |
| − | +----------------+--------------------------------------+
| |
| − | | audited | False |
| |
| − | | description | |
| |
| − | | firewall_rules | a70cf19e-8178-4de6-85e3-6e2610fcc620 |
| |
| − | | | f2349c92-3f1b-4aad-90ed-d6626b80f41e |
| |
| − | | id | e00ce2a6-8387-4c41-9654-641ae6470f56 |
| |
| − | | name | test-policy-east |
| |
| − | | shared | False |
| |
| − | | tenant_id | d98aa7dd12f94af29a4c1d7b8174643c |
| |
| − | +----------------+--------------------------------------+
| |
| − | stack@east-virtual-machine:~/devstack$ neutron firewall-create e00ce2a6-8387-4c41-9654-641ae6470f56
| |
| − | Created a new firewall:
| |
| − | +--------------------+--------------------------------------+
| |
| − | | Field | Value |
| |
| − | +--------------------+--------------------------------------+
| |
| − | | admin_state_up | True |
| |
| − | | description | |
| |
| − | | firewall_policy_id | e00ce2a6-8387-4c41-9654-641ae6470f56 |
| |
| − | | id | b072f9e2-b035-4a26-b9c3-0145800e86b8 |
| |
| − | | name | |
| |
| − | | status | PENDING_CREATE |
| |
| − | | tenant_id | d98aa7dd12f94af29a4c1d7b8174643c |
| |
| − | +--------------------+--------------------------------------+
| |
| − | stack@east-virtual-machine:~/devstack$ neutron firewall-show b072f9e2-b035-4a26-b9c3-0145800e86b8
| |
| − | +--------------------+--------------------------------------+
| |
| − | | Field | Value |
| |
| − | +--------------------+--------------------------------------+
| |
| − | | admin_state_up | True |
| |
| − | | description | |
| |
| − | | firewall_policy_id | e00ce2a6-8387-4c41-9654-641ae6470f56 |
| |
| − | | id | b072f9e2-b035-4a26-b9c3-0145800e86b8 |
| |
| − | | name | |
| |
| − | | status | ACTIVE |
| |
| − | | tenant_id | d98aa7dd12f94af29a4c1d7b8174643c |
| |
| − | +--------------------+--------------------------------------+
| |
| − | stack@east-virtual-machine:~/devstack$ sudo ip netns exec qrouter-2269732f-1e8d-42bb-bed4-7a1f7e101967 ssh cirros@10.1.0.2
| |
| − | cirros@10.1.0.2's password:
| |
| − | $ ping 10.2.0.4
| |
| − | PING 10.2.0.4 (10.2.0.4): 56 data bytes
| |
| − | 64 bytes from 10.2.0.4: seq=0 ttl=62 time=29.759 ms
| |
| − | 64 bytes from 10.2.0.4: seq=1 ttl=62 time=1.480 ms
| |
| − | ^C
| |
| − | --- 10.2.0.4 ping statistics ---
| |
| − | 2 packets transmitted, 2 packets received, 0% packet loss
| |
| − | round-trip min/avg/max = 1.480/15.619/29.759 ms
| |
| − | $ ping 10.2.0.2
| |
| − | PING 10.2.0.2 (10.2.0.2): 56 data bytes
| |
| − | ^C
| |
| − | --- 10.2.0.2 ping statistics ---
| |
| − | 2 packets transmitted, 0 packets received, 100% packet loss
| |
| − | $ exit
| |
| − | Connection to 10.1.0.2 closed.
| |
| − | stack@east-virtual-machine
| |
| − | </nowiki></pre>
| |
| − |
| |
| − | We can actually remove the explicit deny rule for 10.2.0.2 and allow the default deny all to pick that up
| |
| − | <pre><nowiki>
| |
| − | stack@east-virtual-machine:~/devstack$ neutron firewall-rule-list
| |
| − | +--------------------------------------+------+--------------------------------------+------------------------+---------+
| |
| − | | id | name | firewall_policy_id | summary | enabled |
| |
| − | +--------------------------------------+------+--------------------------------------+------------------------+---------+
| |
| − | | a70cf19e-8178-4de6-85e3-6e2610fcc620 | | e00ce2a6-8387-4c41-9654-641ae6470f56 | ICMP, | True |
| |
| − | | | | | source: none(none), | |
| |
| − | | | | | dest: 10.2.0.4(none), | |
| |
| − | | | | | allow | |
| |
| − | | f2349c92-3f1b-4aad-90ed-d6626b80f41e | | e00ce2a6-8387-4c41-9654-641ae6470f56 | ICMP, | True |
| |
| − | | | | | source: none(none), | |
| |
| − | | | | | dest: 10.2.0.2(none), | |
| |
| − | | | | | deny | |
| |
| − | +--------------------------------------+------+--------------------------------------+------------------------+---------+
| |
| − | stack@east-virtual-machine:~/devstack$ neutron firewall-policy-remove-rule e00ce2a6-8387-4c41-9654-641ae6470f56 f2349c92-3f1b-4aad-90ed-d6626b80f41e
| |
| − | Removed firewall rule from firewall policy e00ce2a6-8387-4c41-9654-641ae6470f56
| |
| − | stack@east-virtual-machine:~/devstack$ neutron firewall-policy-show test-policy-east
| |
| − | +----------------+--------------------------------------+
| |
| − | | Field | Value |
| |
| − | +----------------+--------------------------------------+
| |
| − | | audited | False |
| |
| − | | description | |
| |
| − | | firewall_rules | a70cf19e-8178-4de6-85e3-6e2610fcc620 |
| |
| − | | id | e00ce2a6-8387-4c41-9654-641ae6470f56 |
| |
| − | | name | test-policy-east |
| |
| − | | shared | False |
| |
| − | | tenant_id | d98aa7dd12f94af29a4c1d7b8174643c |
| |
| − | +----------------+--------------------------------------+
| |
| − | stack@east-virtual-machine:~/devstack$ sudo ip netns exec qrouter-2269732f-1e8d-42bb-bed4-7a1f7e101967 ssh cirros@10.1.0.2
| |
| − | cirros@10.1.0.2's password:
| |
| − | $ ping 10.2.0.2
| |
| − | PING 10.2.0.2 (10.2.0.2): 56 data bytes
| |
| − | ^C
| |
| − | --- 10.2.0.2 ping statistics ---
| |
| − | 2 packets transmitted, 0 packets received, 100% packet loss
| |
| − | $ ping 10.2.0.4
| |
| − | PING 10.2.0.4 (10.2.0.4): 56 data bytes
| |
| − | 64 bytes from 10.2.0.4: seq=0 ttl=62 time=23.280 ms
| |
| − | 64 bytes from 10.2.0.4: seq=1 ttl=62 time=1.545 ms
| |
| − | ^C
| |
| − | --- 10.2.0.4 ping statistics ---
| |
| − | 2 packets transmitted, 2 packets received, 0% packet loss
| |
| − | round-trip min/avg/max = 1.545/12.412/23.280 ms
| |
| − | $
| |
| − | </nowiki></pre>
| |
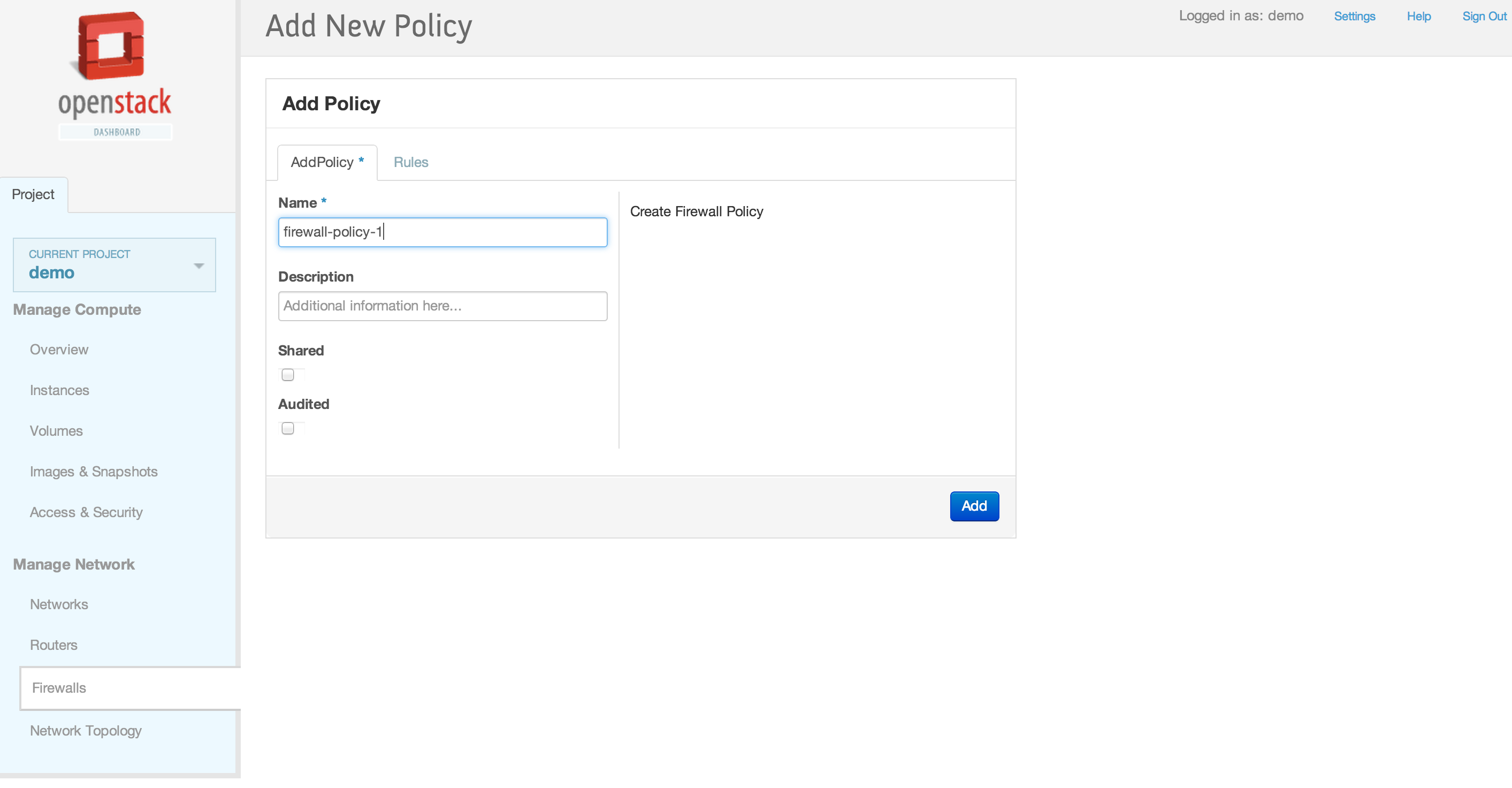
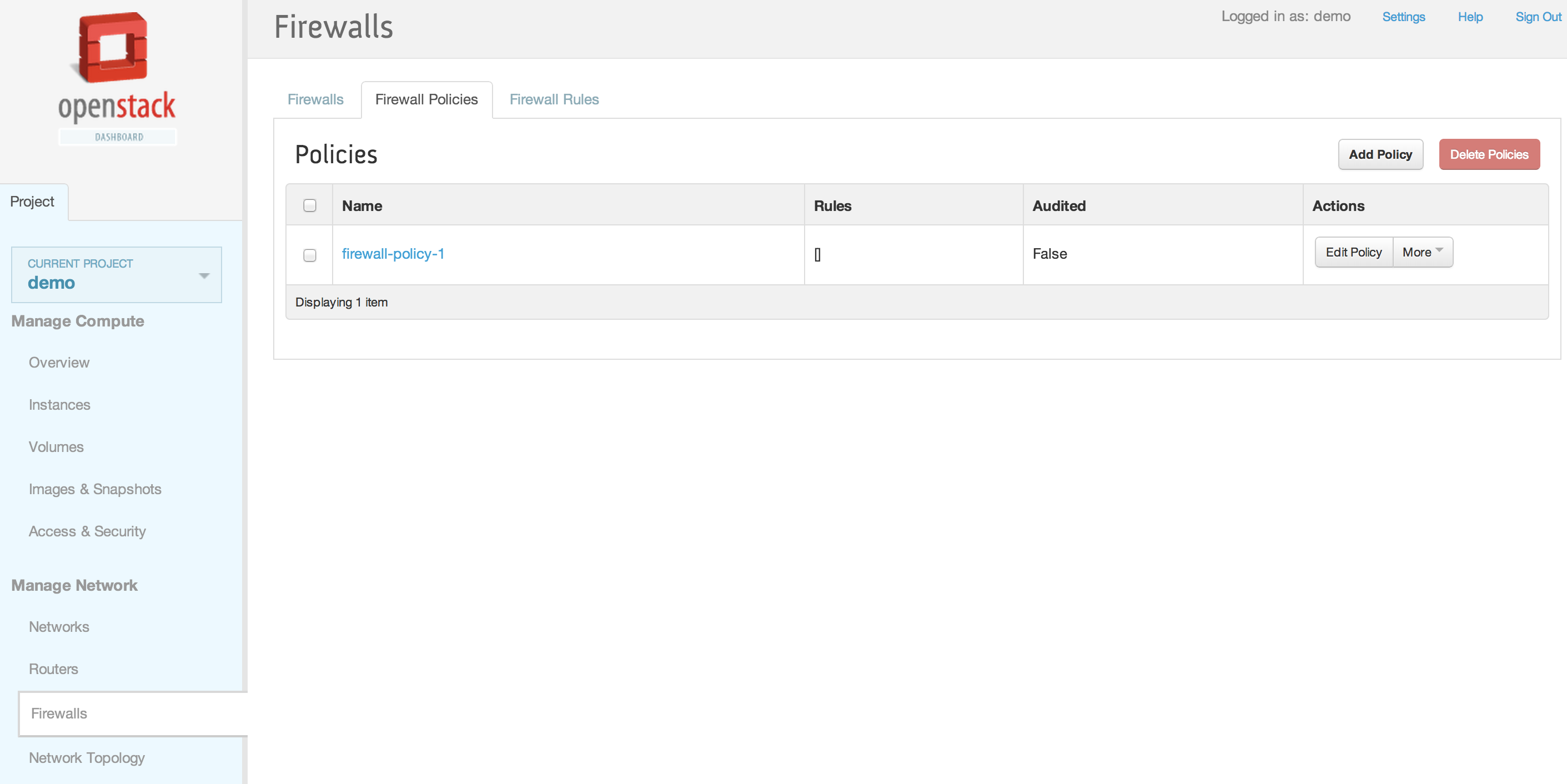
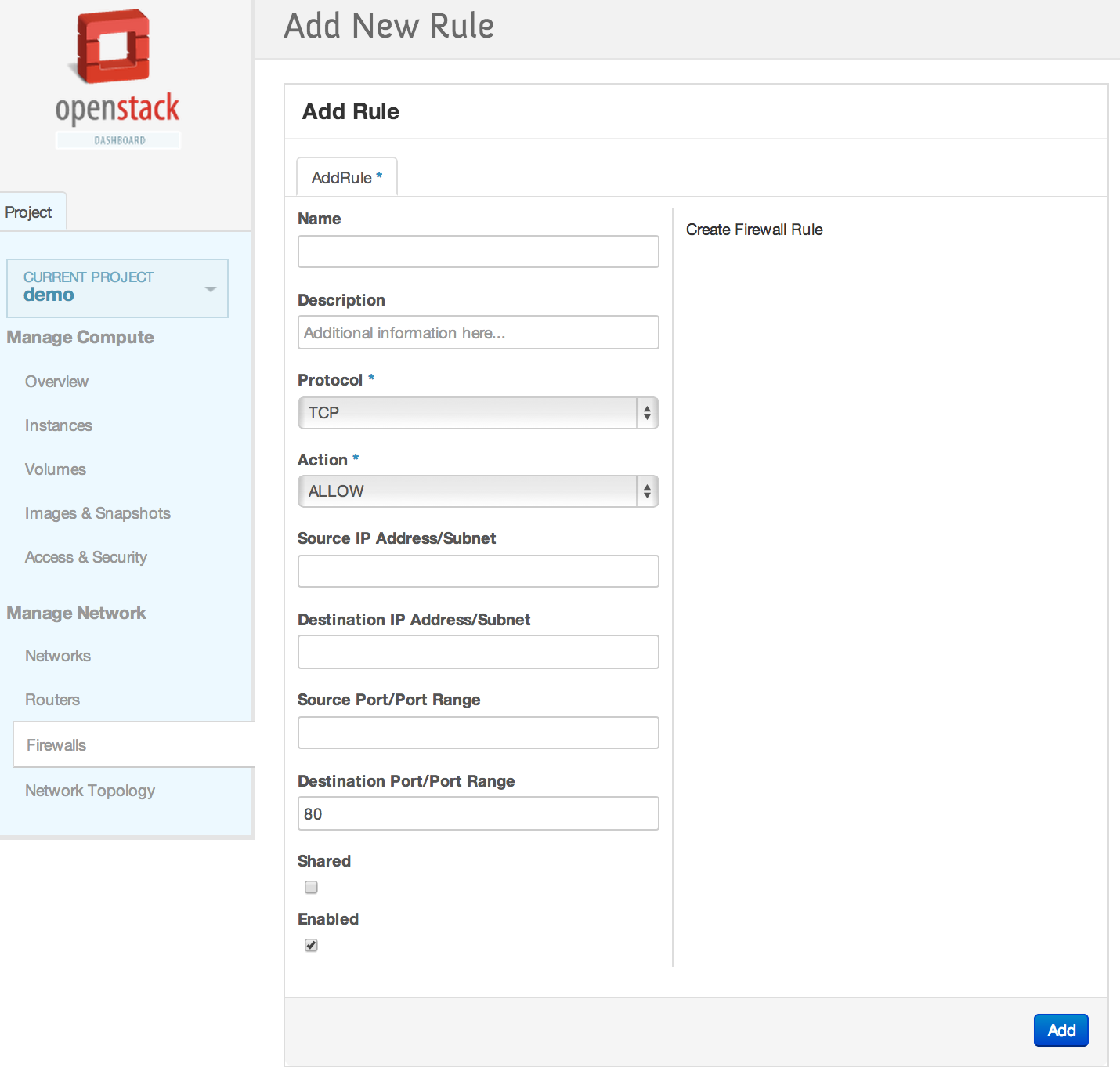
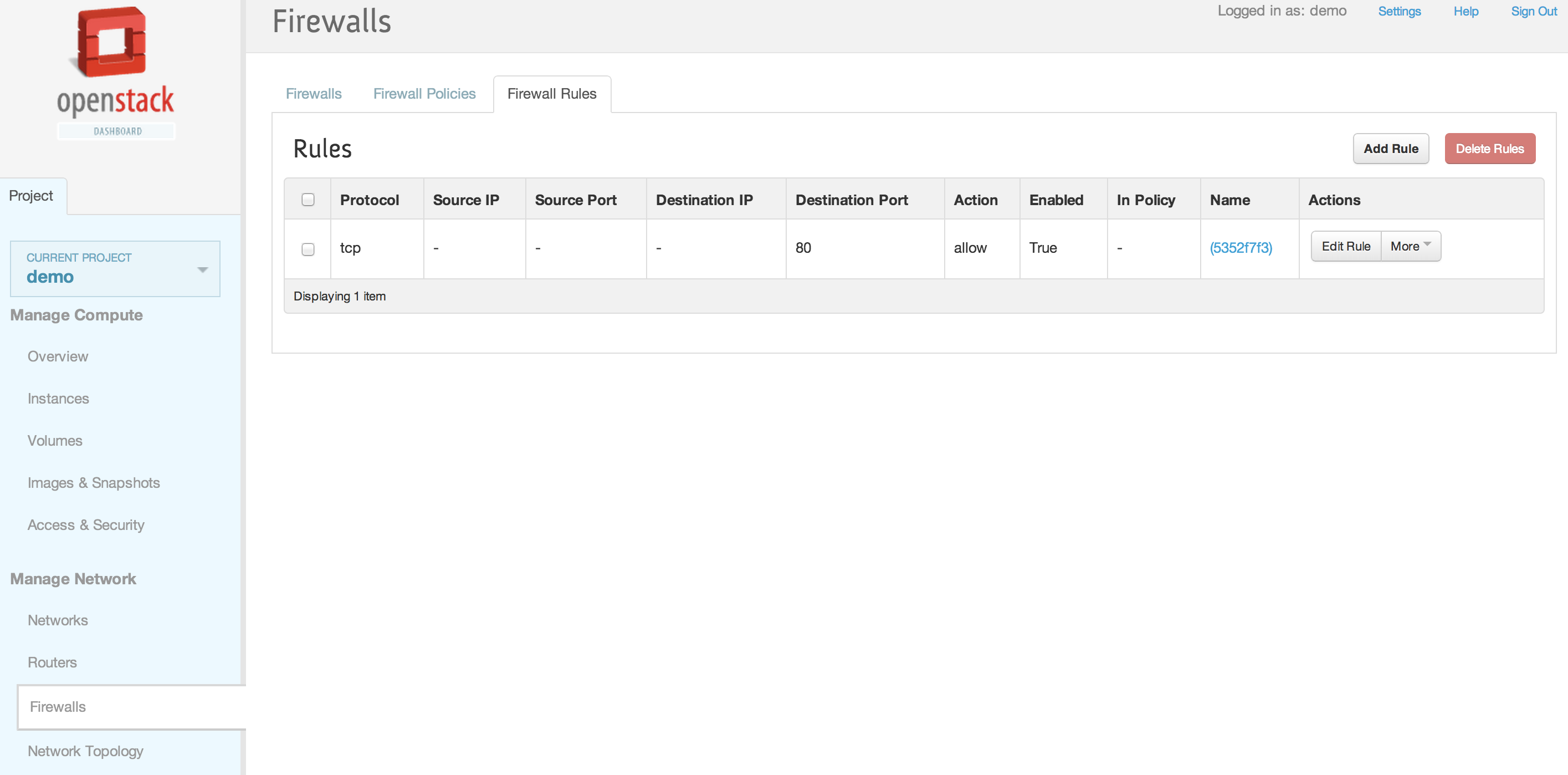
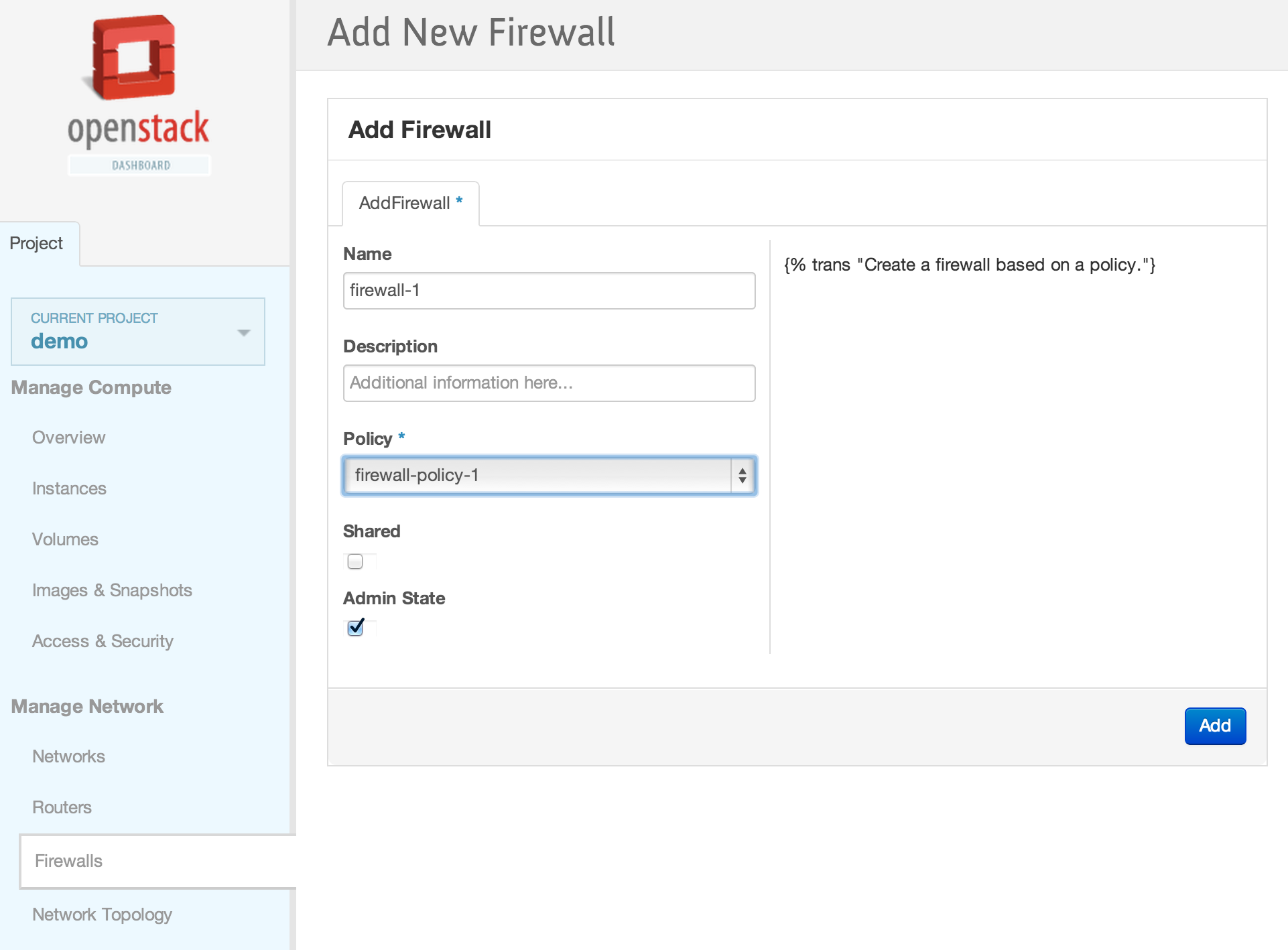
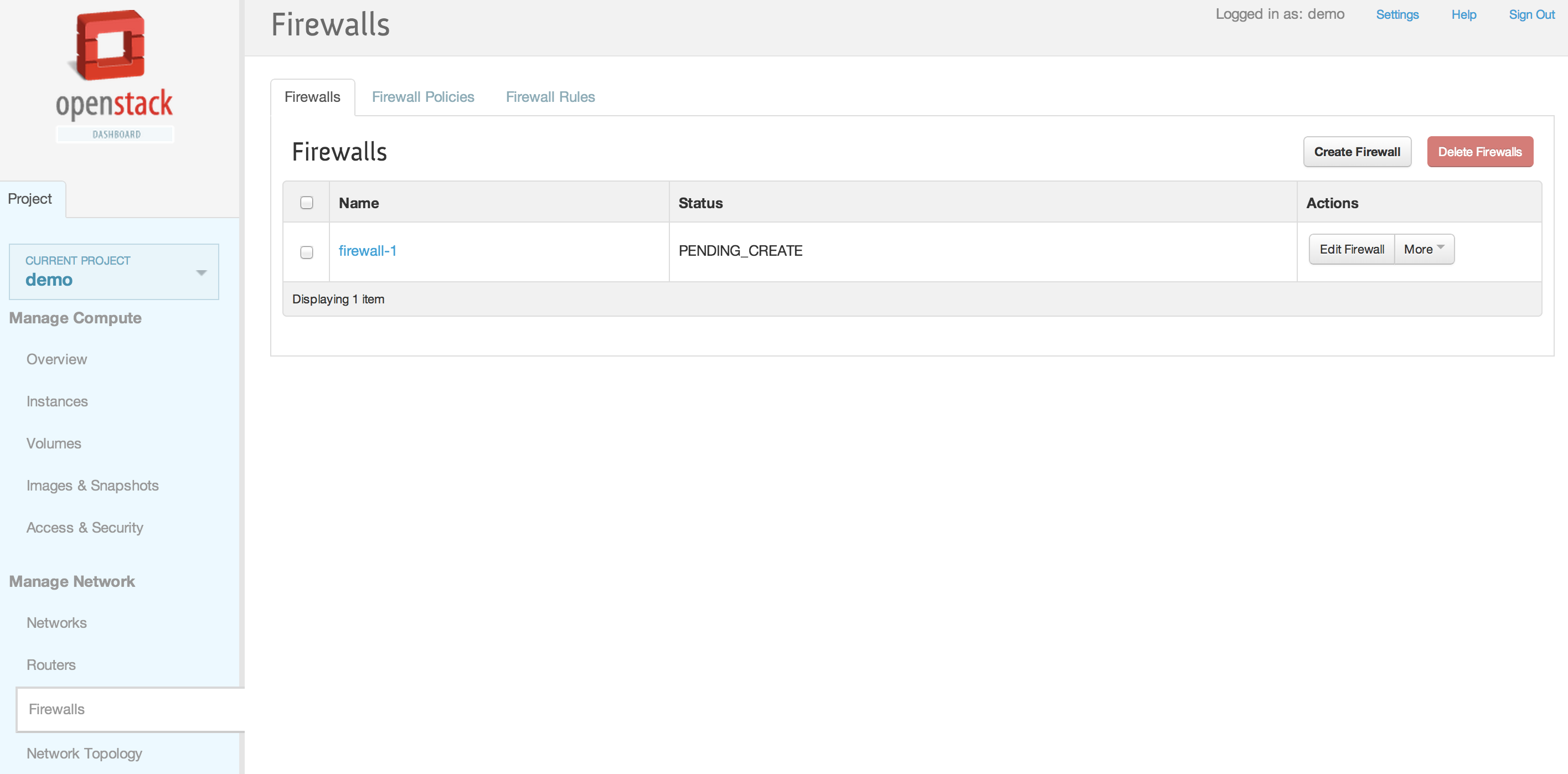
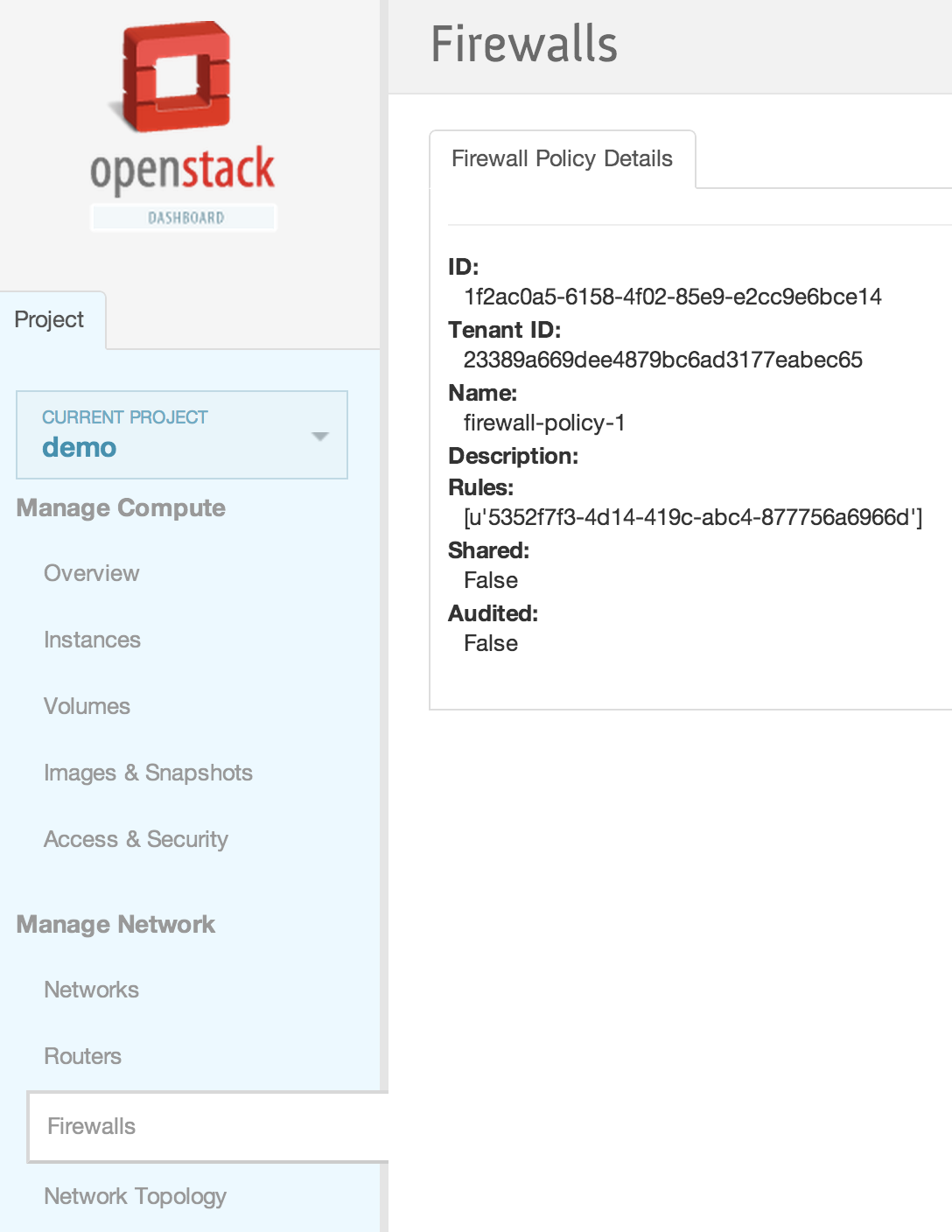
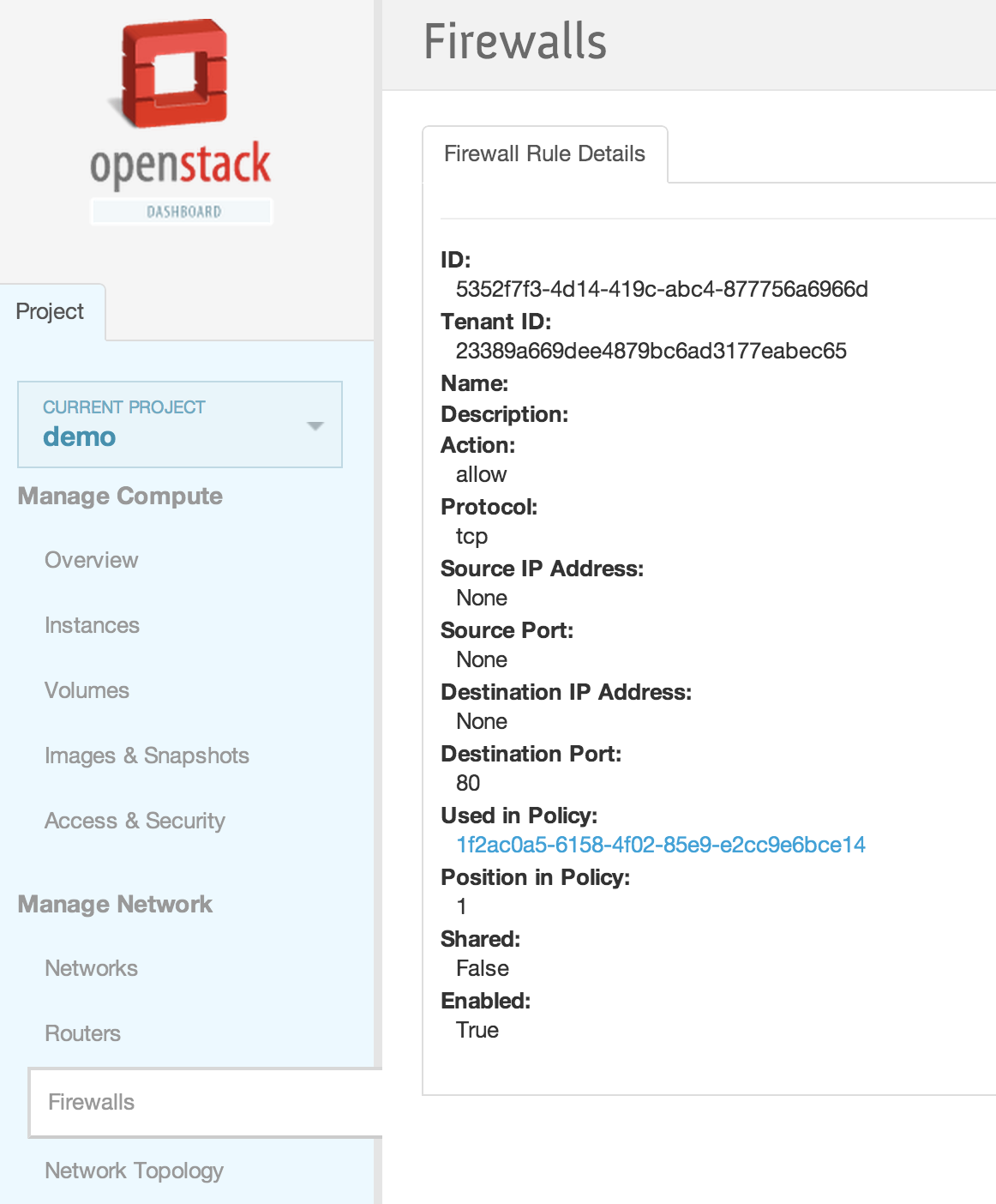
| | | | |
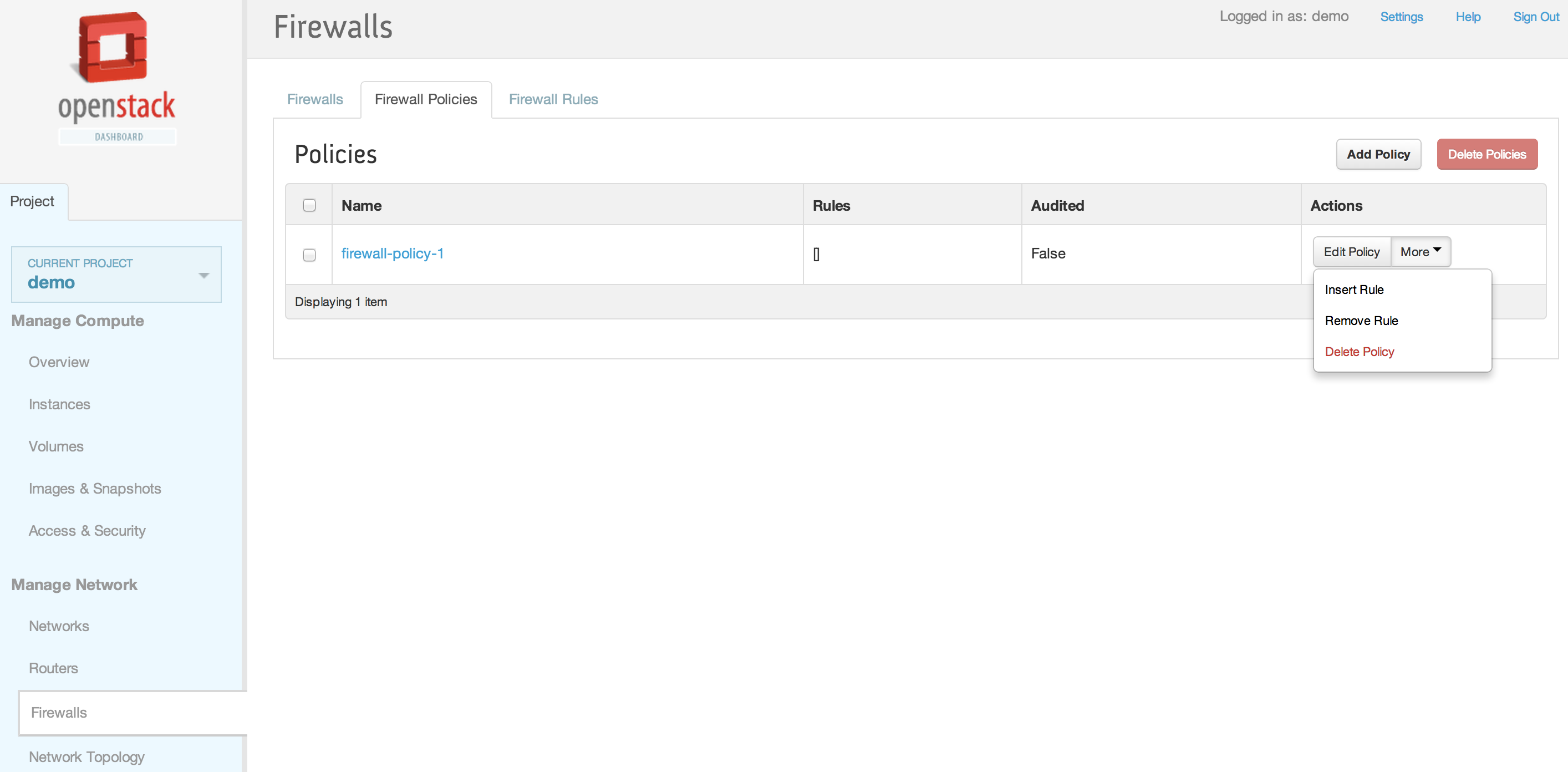
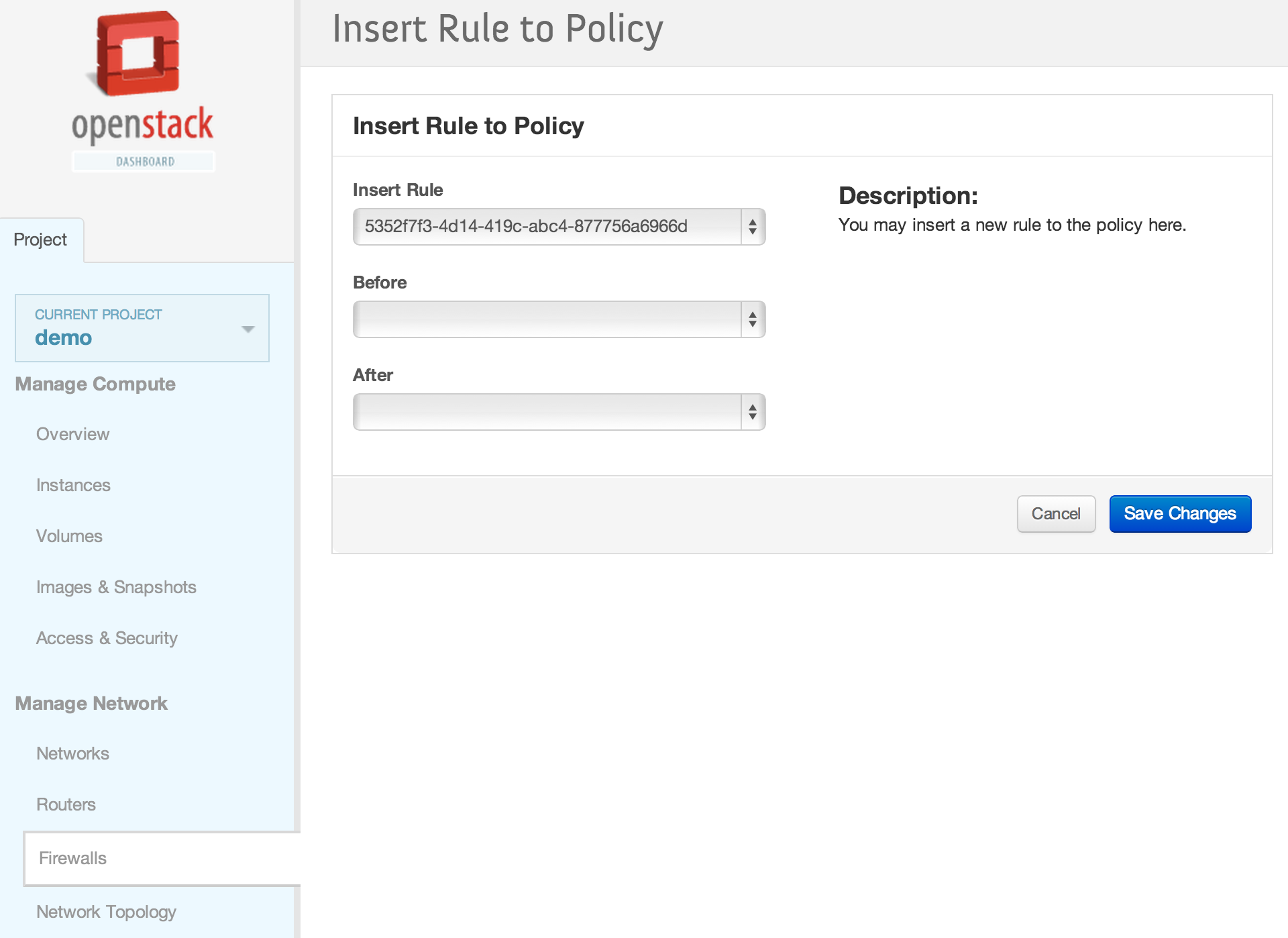
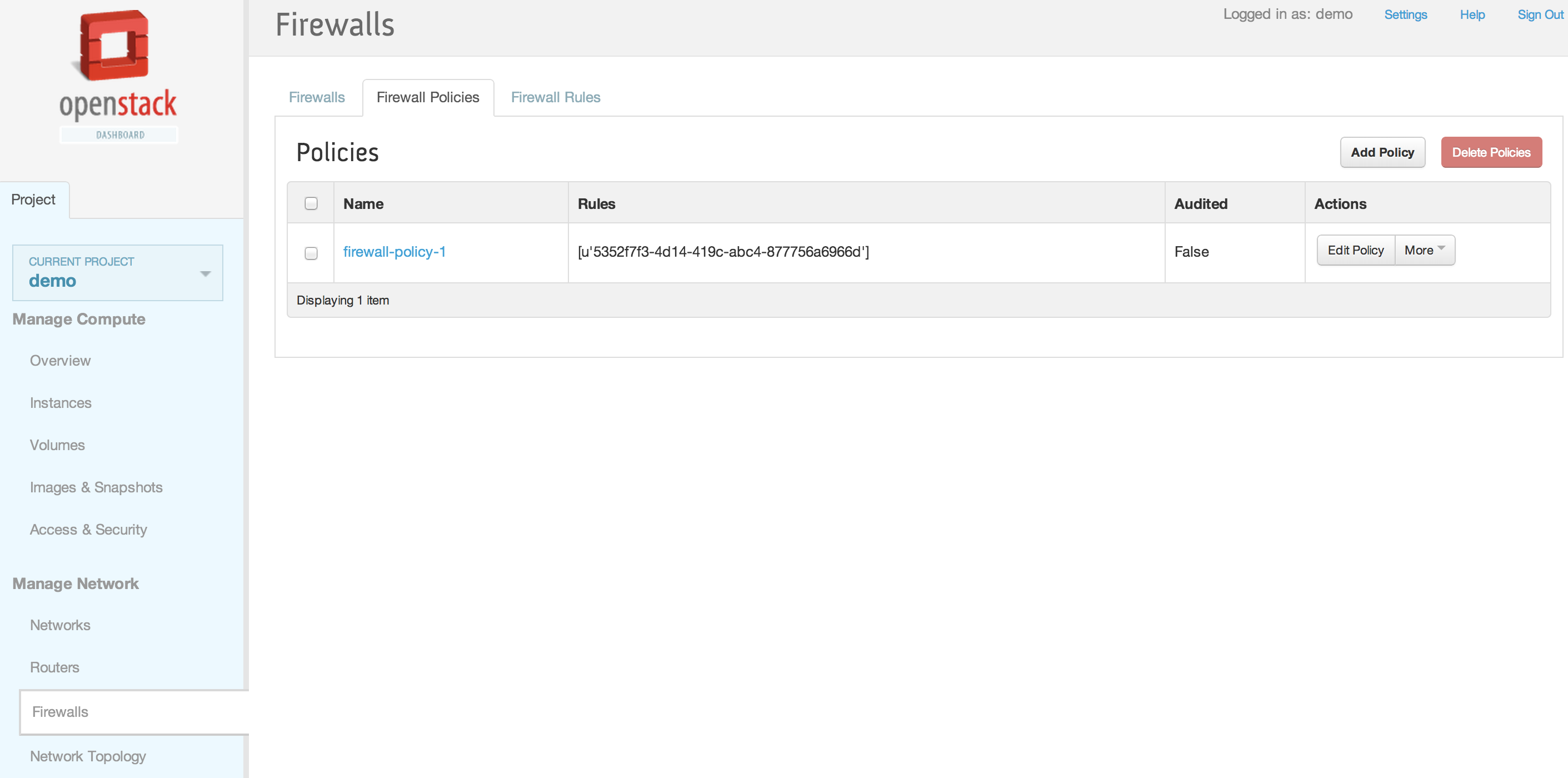
| | == Horizon Interface == | | == Horizon Interface == |