Difference between revisions of "Neutron/FWaaS/HowToInstall"
Rajesh.mohan (talk | contribs) (→REST calls using curl:) |
|||
| (40 intermediate revisions by 7 users not shown) | |||
| Line 1: | Line 1: | ||
| − | == | + | == Trying out FWaaS using Devstack== |
| + | Add these lines in localrc: | ||
| − | + | enable_service q-fwaas | |
| − | + | ||
| − | + | Q_SERVICE_PLUGIN_CLASSES=neutron.services.firewall.fwaas_plugin.FirewallPlugin | |
| − | |||
| − | |||
| − | + | * The following will be populated by after the devstack installation: | |
| − | |||
| − | + | /etc/neutron/l3_agent.ini | |
| − | + | <pre><nowiki> | |
| + | [fwaas] | ||
| + | driver = neutron_fwaas.services.firewall.drivers.linux.iptables_fwaas.IptablesFwaasDriver | ||
| + | enabled = True | ||
| + | </nowiki></pre> | ||
| − | == | + | == CLI/REST Walkthrough == |
| + | === CLI === | ||
| − | * | + | * To list firewalls, firewall_policies, firewall_rules: |
| − | / | + | <pre><nowiki> |
| + | neutron firewall-list | ||
| + | neutron firewall-policy-list | ||
| + | neutron firewall-rule-list | ||
| + | </nowiki></pre> | ||
| − | + | * Create firewall rule: | |
| − | + | <pre><nowiki> | |
| − | + | neutron firewall-rule-create --protocol tcp --destination-port 80 --action allow | |
| − | + | Created a new firewall_rule: | |
| + | +------------------------+--------------------------------------+ | ||
| + | | Field | Value | | ||
| + | +------------------------+--------------------------------------+ | ||
| + | | action | allow | | ||
| + | | description | | | ||
| + | | destination_ip_address | | | ||
| + | | destination_port | 80 | | ||
| + | | enabled | True | | ||
| + | | firewall_policy_id | | | ||
| + | | id | 1283a548-9ca8-4a7b-a187-fc21c7fefe8e | | ||
| + | | ip_version | 4 | | ||
| + | | name | | | ||
| + | | position | | | ||
| + | | protocol | tcp | | ||
| + | | shared | False | | ||
| + | | source_ip_address | | | ||
| + | | source_port | | | ||
| + | | tenant_id | baaaf4da44874e3f82ff93beba64117e | | ||
| + | +------------------------+--------------------------------------+ | ||
| + | </nowiki></pre> | ||
| + | * Create firewall policy with rules: | ||
| − | + | <pre><nowiki> | |
| + | neutron firewall-policy-create --firewall-rules "1283a548-9ca8-4a7b-a187-fc21c7fefe8e ef9fe8d1-1d79-485b-9d90-d1dd4bf228b5" test-policy | ||
| + | Created a new firewall_policy: | ||
| + | +----------------+--------------------------------------+ | ||
| + | | Field | Value | | ||
| + | +----------------+--------------------------------------+ | ||
| + | | audited | False | | ||
| + | | description | | | ||
| + | | firewall_rules | 1283a548-9ca8-4a7b-a187-fc21c7fefe8e | | ||
| + | | | ef9fe8d1-1d79-485b-9d90-d1dd4bf228b5 | | ||
| + | | id | 257f0a59-5b16-486b-aae2-b57c60e2053f | | ||
| + | | name | test-policy | | ||
| + | | shared | False | | ||
| + | | tenant_id | baaaf4da44874e3f82ff93beba64117e | | ||
| + | +----------------+--------------------------------------+ | ||
| + | </nowiki></pre> | ||
| − | + | * Create the firewall with the policy association: | |
| − | + | <pre><nowiki> | |
| + | neutron firewall-create 257f0a59-5b16-486b-aae2-b57c60e2053f | ||
| + | Created a new firewall: | ||
| + | +--------------------+--------------------------------------+ | ||
| + | | Field | Value | | ||
| + | +--------------------+--------------------------------------+ | ||
| + | | admin_state_up | True | | ||
| + | | description | | | ||
| + | | firewall_policy_id | 257f0a59-5b16-486b-aae2-b57c60e2053f | | ||
| + | | id | 28530399-d8ee-4700-9685-ee5d645f4d59 | | ||
| + | | name | | | ||
| + | | status | PENDING_CREATE | | ||
| + | | tenant_id | baaaf4da44874e3f82ff93beba64117e | | ||
| + | +--------------------+--------------------------------------+ | ||
| + | </nowiki></pre> | ||
| − | + | * Check that the firewall is in ACTIVE state before the next operation can be performed on the firewall: | |
| − | + | <pre><nowiki> | |
| − | + | neutron firewall-show 28530399-d8ee-4700-9685-ee5d645f4d59 | |
| + | +--------------------+--------------------------------------+ | ||
| + | | Field | Value | | ||
| + | +--------------------+--------------------------------------+ | ||
| + | | admin_state_up | True | | ||
| + | | description | | | ||
| + | | firewall_policy_id | 257f0a59-5b16-486b-aae2-b57c60e2053f | | ||
| + | | id | 28530399-d8ee-4700-9685-ee5d645f4d59 | | ||
| + | | name | | | ||
| + | | status | ACTIVE | | ||
| + | | tenant_id | baaaf4da44874e3f82ff93beba64117e | | ||
| + | +--------------------+--------------------------------------+ | ||
| + | </nowiki></pre> | ||
| − | + | * Delete the firewall: | |
| − | + | <pre><nowiki> | |
| + | neutron firewall-delete 28530399-d8ee-4700-9685-ee5d645f4d59 | ||
| + | Deleted firewall: 28530399-d8ee-4700-9685-ee5d645f4d59 | ||
| + | </nowiki></pre> | ||
| − | == | + | === REST calls using curl: === |
| + | export q_url=http://<neutron-server-ip>:9696/v2.0 | ||
| − | + | for example | |
| − | export q_url=http:// | + | export q_url=http://127.0.0.1:9696/v2.0 |
and | and | ||
| − | export auth_token=<auth_token> | + | export auth_token=<auth_token> |
where <auth_token> is the token obtained from: | where <auth_token> is the token obtained from: | ||
| Line 67: | Line 140: | ||
* To list firewalls, firewall_policies, firewall_rules: | * To list firewalls, firewall_policies, firewall_rules: | ||
| − | curl -X GET -H "X-Auth-Token: $auth_token" $q_url/fw/firewalls | python -mjson.tool | + | curl -X GET -H "X-Auth-Token: $auth_token" $q_url/fw/firewalls | python -mjson.tool |
| − | curl -X GET -H "X-Auth-Token: $auth_token" $q_url/fw/firewall_policies | python -mjson.tool | + | curl -X GET -H "X-Auth-Token: $auth_token" $q_url/fw/firewall_policies | python -mjson.tool |
| − | curl -X GET -H "X-Auth-Token: $auth_token" $q_url/fw/firewall_rules | python -mjson.tool | + | curl -X GET -H "X-Auth-Token: $auth_token" $q_url/fw/firewall_rules | python -mjson.tool |
* Create firewall rule: | * Create firewall rule: | ||
| − | curl -X POST -H "X-Auth-Token: $auth_token" -H "Content-type:application/json" -d '{"firewall_rule": {"protocol": "tcp", "destination_port": "80", "action": "allow"}}' $q_url/fw/firewall_rules | + | curl -X POST -H "X-Auth-Token: $auth_token" -H "Content-type:application/json" -d '{"firewall_rule": {"protocol": "tcp", "destination_port": "80", "action": "allow"}}' $q_url/fw/firewall_rules |
| − | * Create | + | * Create firewall policy: |
| − | curl -X POST -H "X-Auth-Token: $auth_token" -H "Content-type:application/json" -d '{"firewall_policy": {"name": "fwasspolicy"} }' $q_url/fw/firewall_policies | + | curl -X POST -H "X-Auth-Token: $auth_token" -H "Content-type:application/json" -d '{"firewall_policy": {"name": "fwasspolicy"} }' $q_url/fw/firewall_policies |
* Add rule to policy (this could have been done while creating the firewall policy too): | * Add rule to policy (this could have been done while creating the firewall policy too): | ||
| − | curl -X PUT -H "X-Auth-Token: $auth_token" -H "Content-type:application/json" -d '{"firewall_policy": {" | + | curl -X PUT -H "X-Auth-Token: $auth_token" -H "Content-type:application/json" -d '{"firewall_policy": {"firewall_rules": ["1d47c609-8fd1-4aad-97fd-157887c47b4f"]}}' $q_url/fw/firewall_policies/9c50d2d0-3a85-4ed7-a20f-bef8c08233e3 |
* Create the firewall with the policy association: | * Create the firewall with the policy association: | ||
| − | curl -X POST -H "X-Auth-Token: $auth_token" -H "Content-type:application/json" -d '{"firewall": {"name": "fwasstest", "firewall_policy_id": "9c50d2d0-3a85-4ed7-a20f-bef8c08233e3"} }' $q_url/fw/firewalls | + | curl -X POST -H "X-Auth-Token: $auth_token" -H "Content-type:application/json" -d '{"firewall": {"name": "fwasstest", "firewall_policy_id": "9c50d2d0-3a85-4ed7-a20f-bef8c08233e3"} }' $q_url/fw/firewalls |
* Delete the firewall: | * Delete the firewall: | ||
| − | curl -X DELETE -H "X-Auth-Token: $auth_token" $q_url/fw/firewalls/9649548e-b87f-4c56-bbb7-5ee84b316da1 | + | curl -X DELETE -H "X-Auth-Token: $auth_token" $q_url/fw/firewalls/9649548e-b87f-4c56-bbb7-5ee84b316da1 |
| − | |||
| − | |||
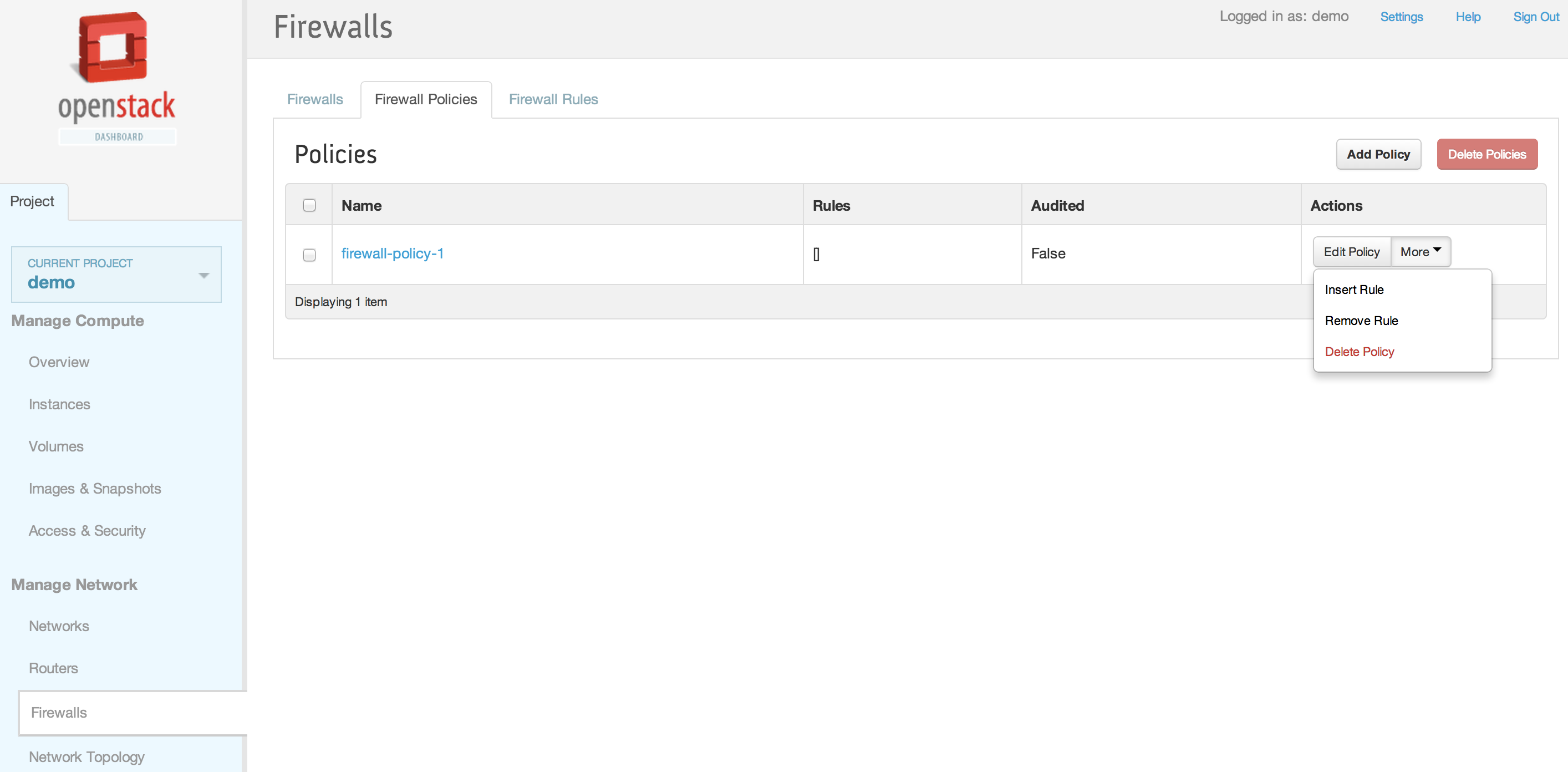
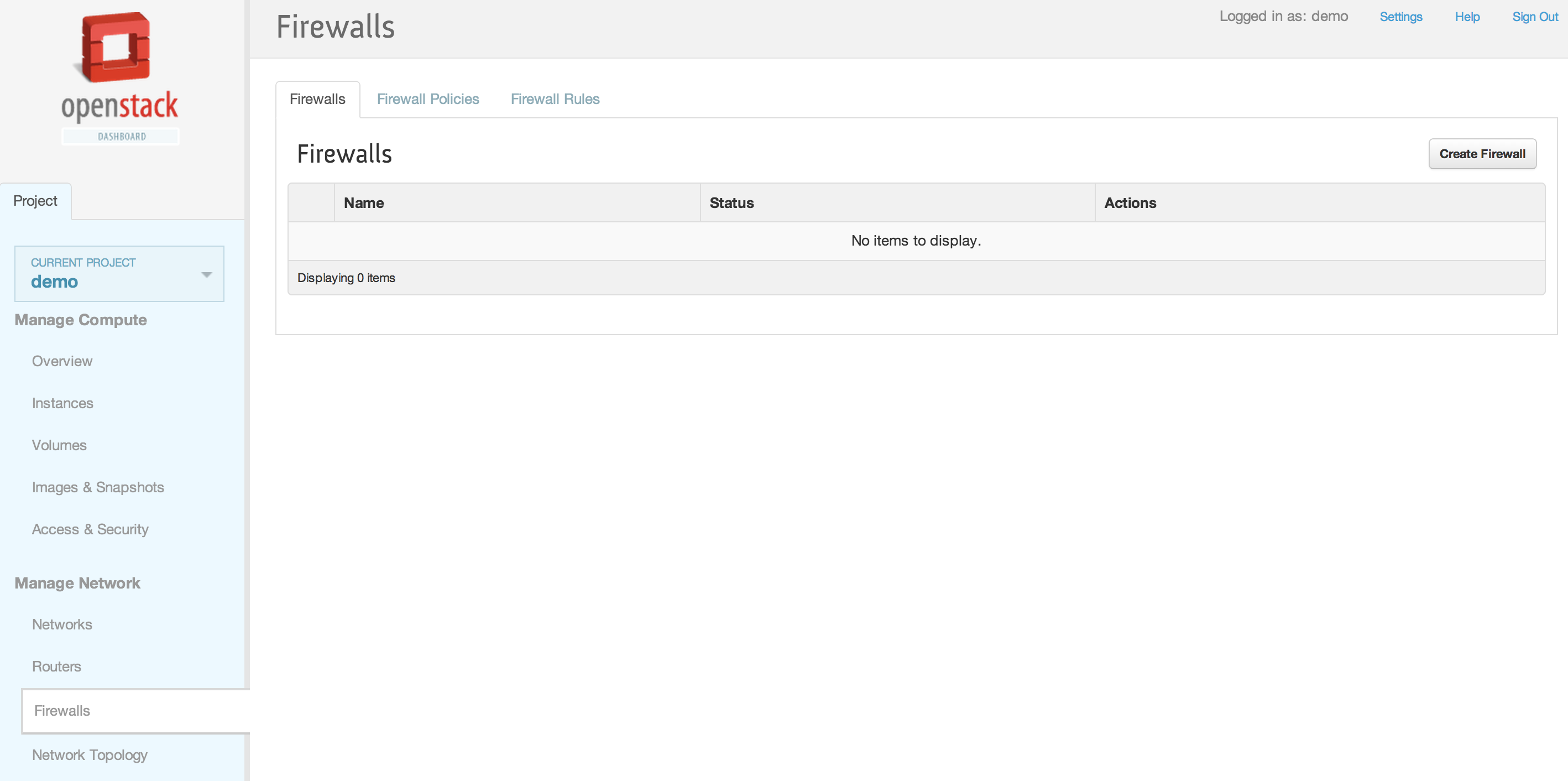
| − | == | + | == Horizon Interface == |
| + | <br /> | ||
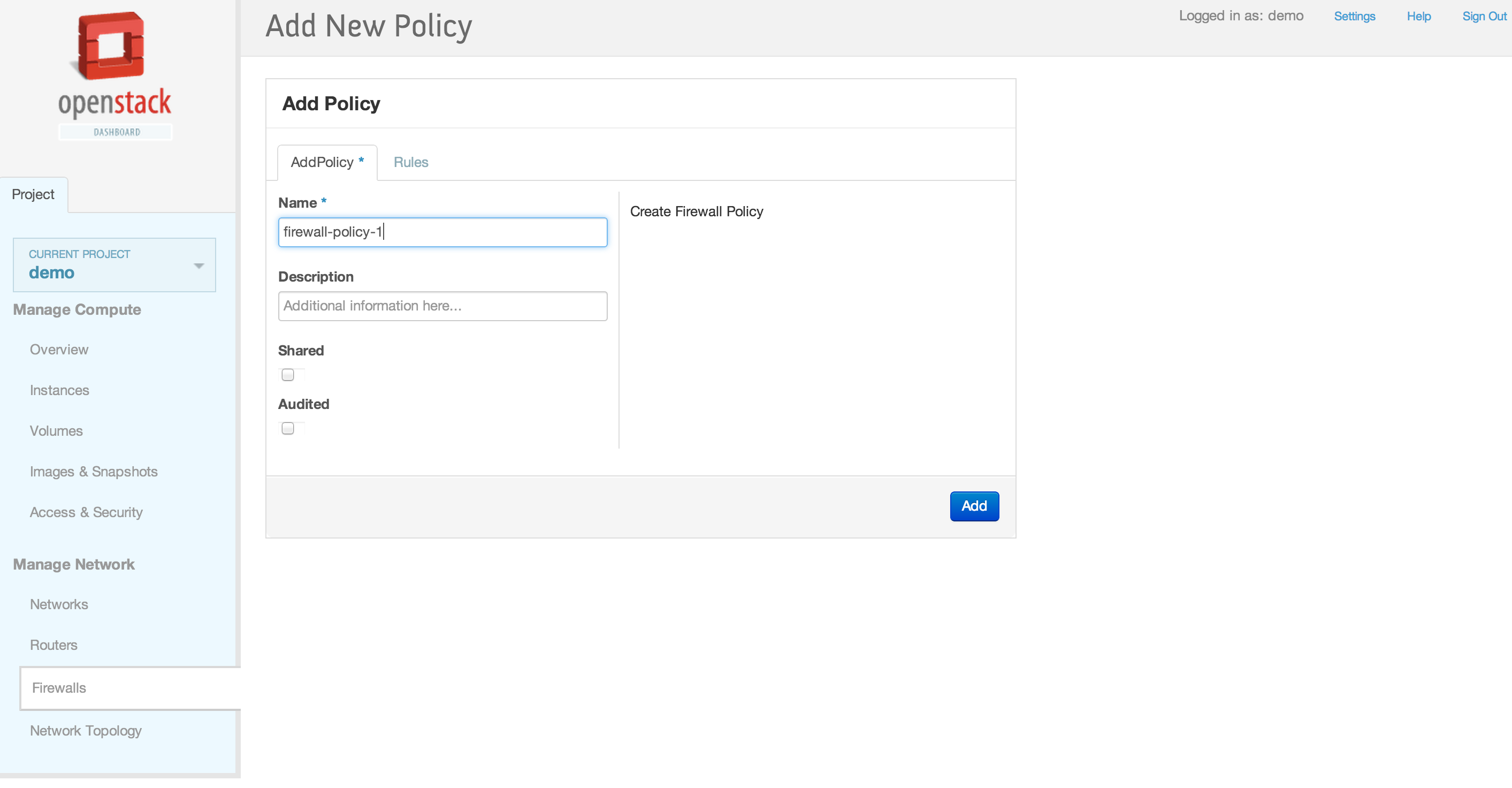
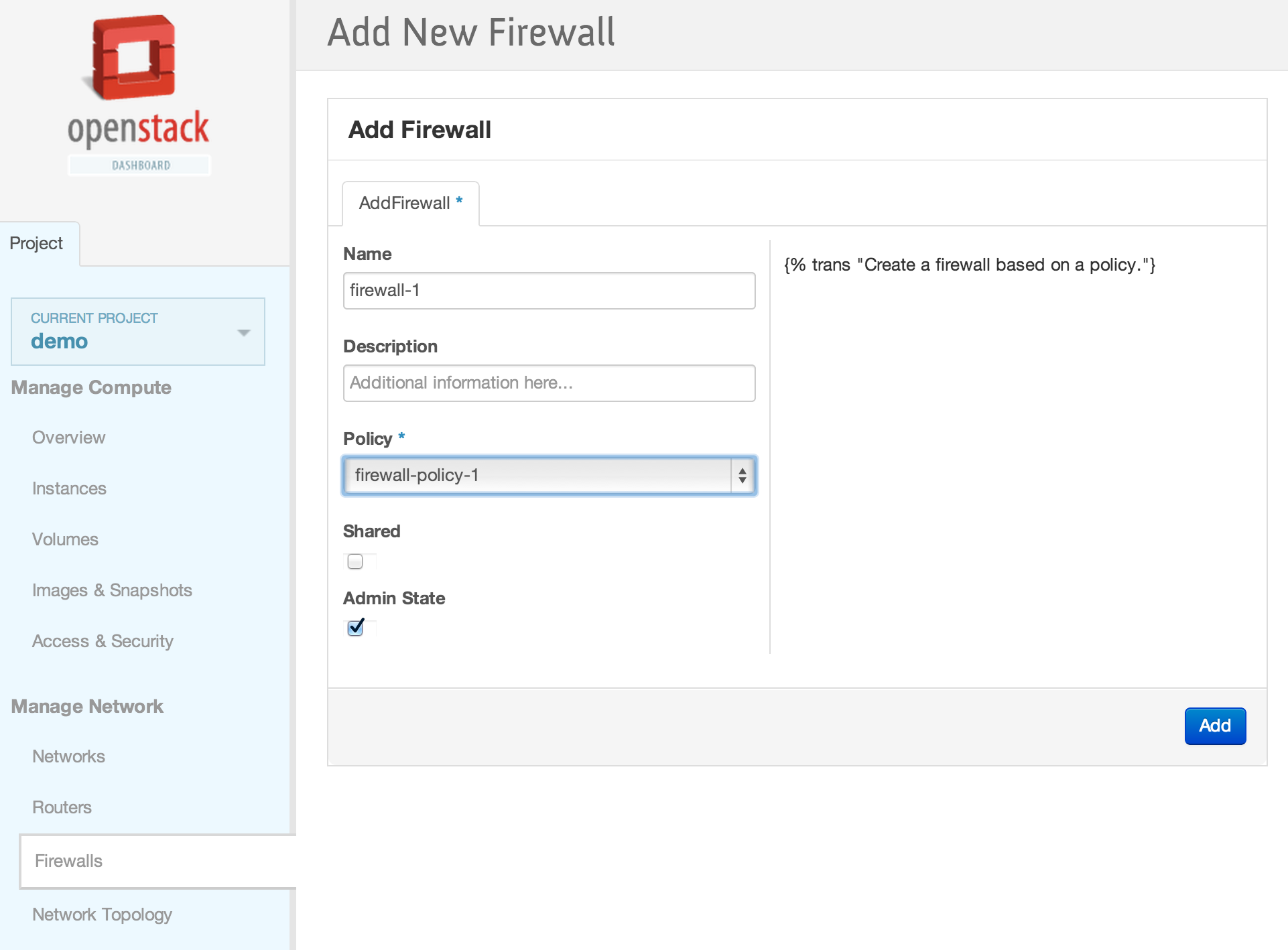
| + | [[File:2013-09-04 11.08.38 pm.png|1000x521px|framed|left|1. Neutron Firewall as a Service (FWaaS) Panel]] | ||
| + | <br /> | ||
| + | [[File:2013-09-04 11.36.54 pm.png|1000x521px|framed|left|2. Add new firewall policy]] | ||
| + | <br /> | ||
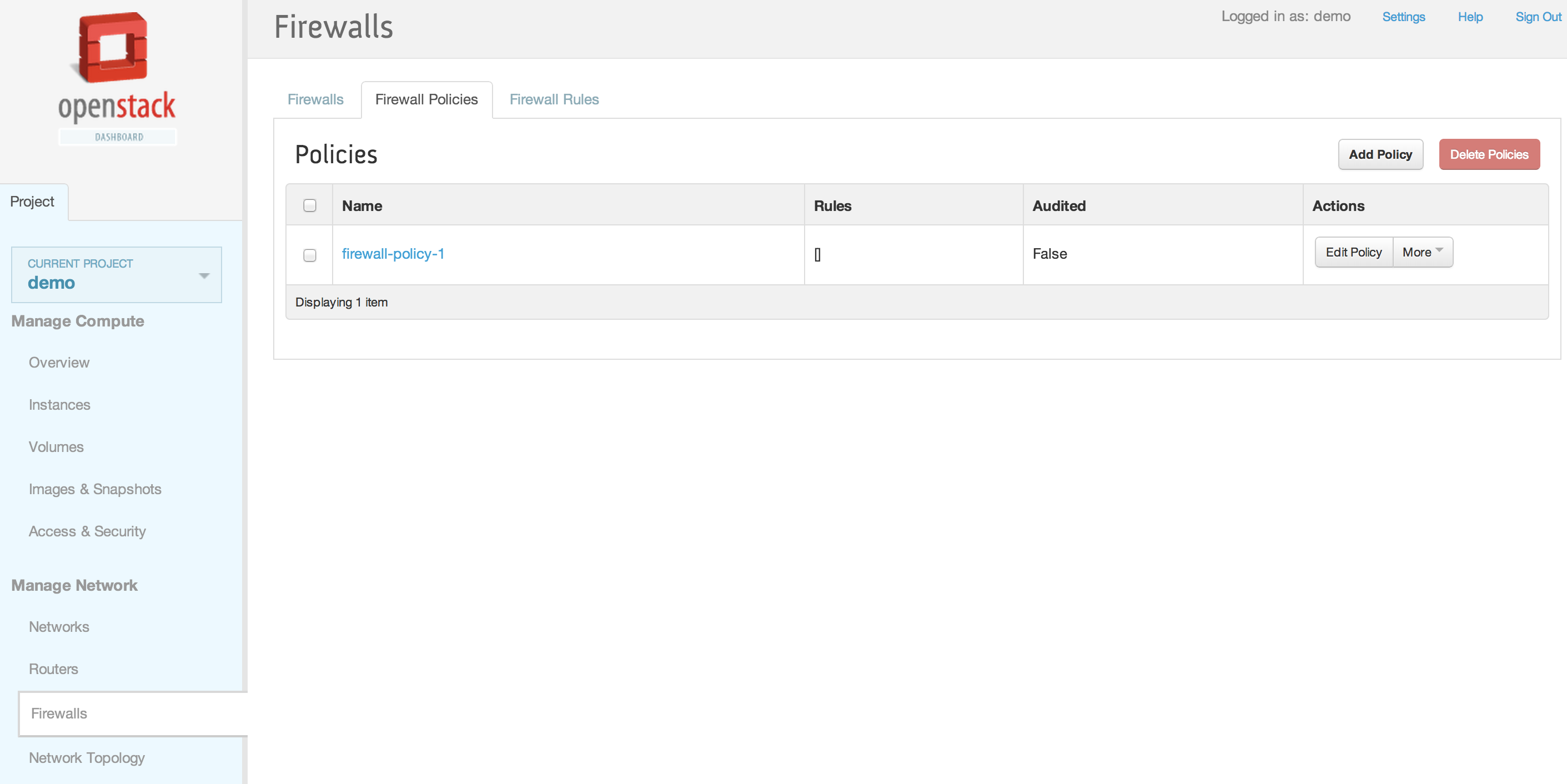
| + | [[File:2013-09-04 11.37.45 pm.png|1000x521px|framed|left|3. New firewall policy added]] | ||
| + | <br /> | ||
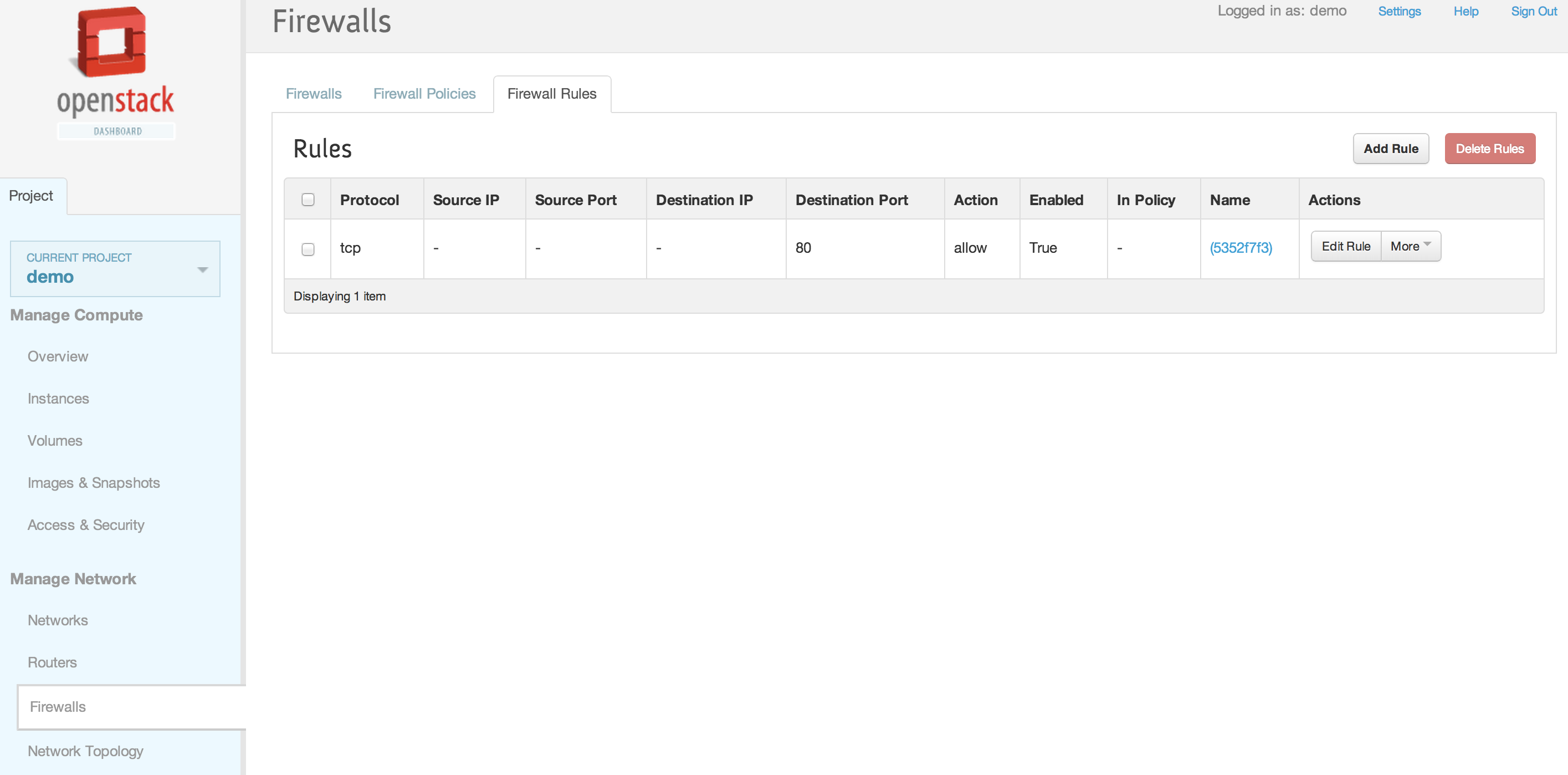
| + | [[File:2013-09-04 11.38.16 pm.png|1000x521px|framed|left|4. Firewall Rules]] | ||
| + | <br /> | ||
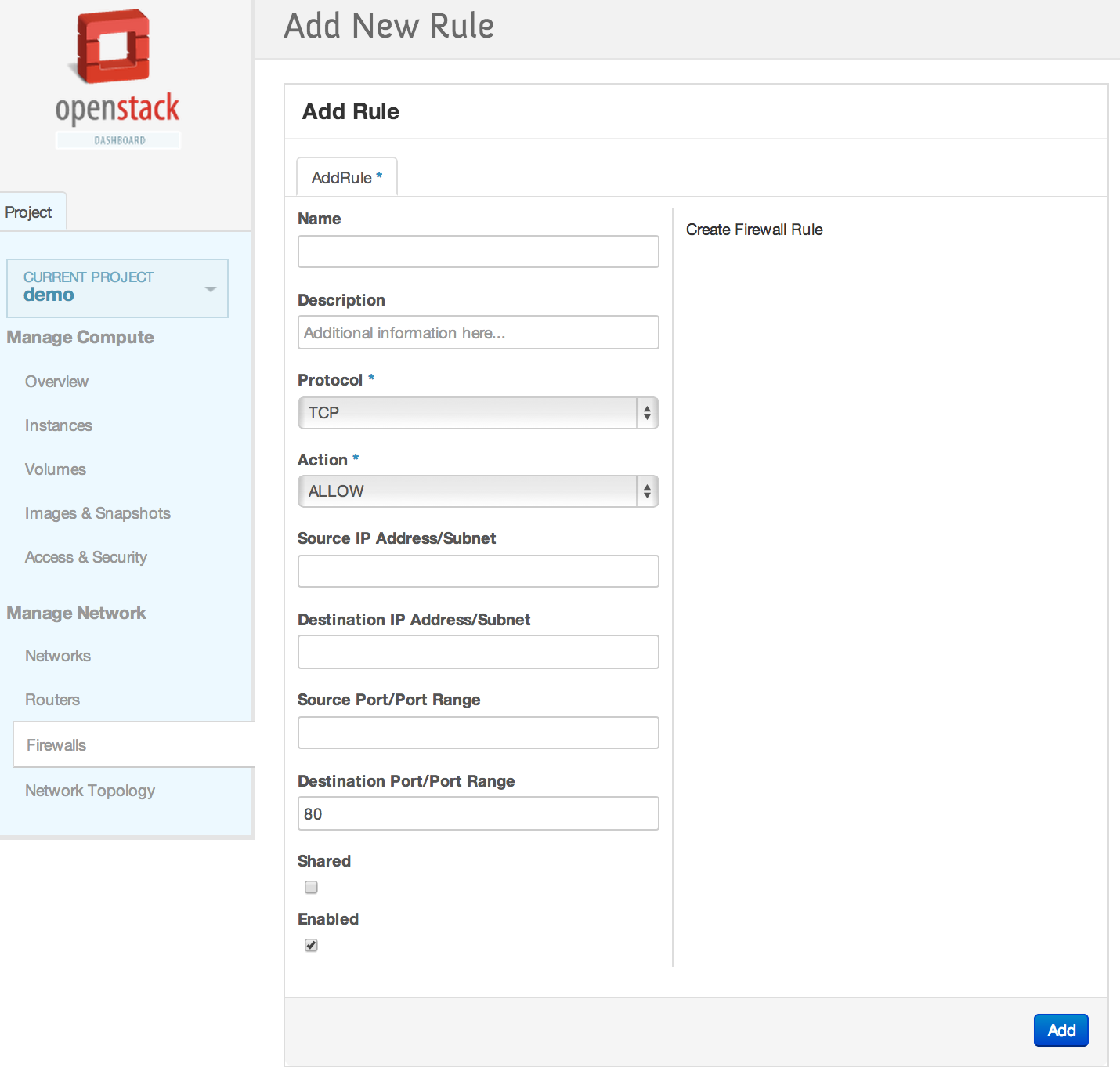
| + | [[File:2013-09-04 11.39.48 pm.png|1000x521px|framed|left|5. Add a new firewall rule]] | ||
| + | <br /> | ||
| + | [[File:2013-09-04 11.40.19 pm.png|1000x521px|framed|left|6. New firewall rule added]] | ||
| + | <br /> | ||
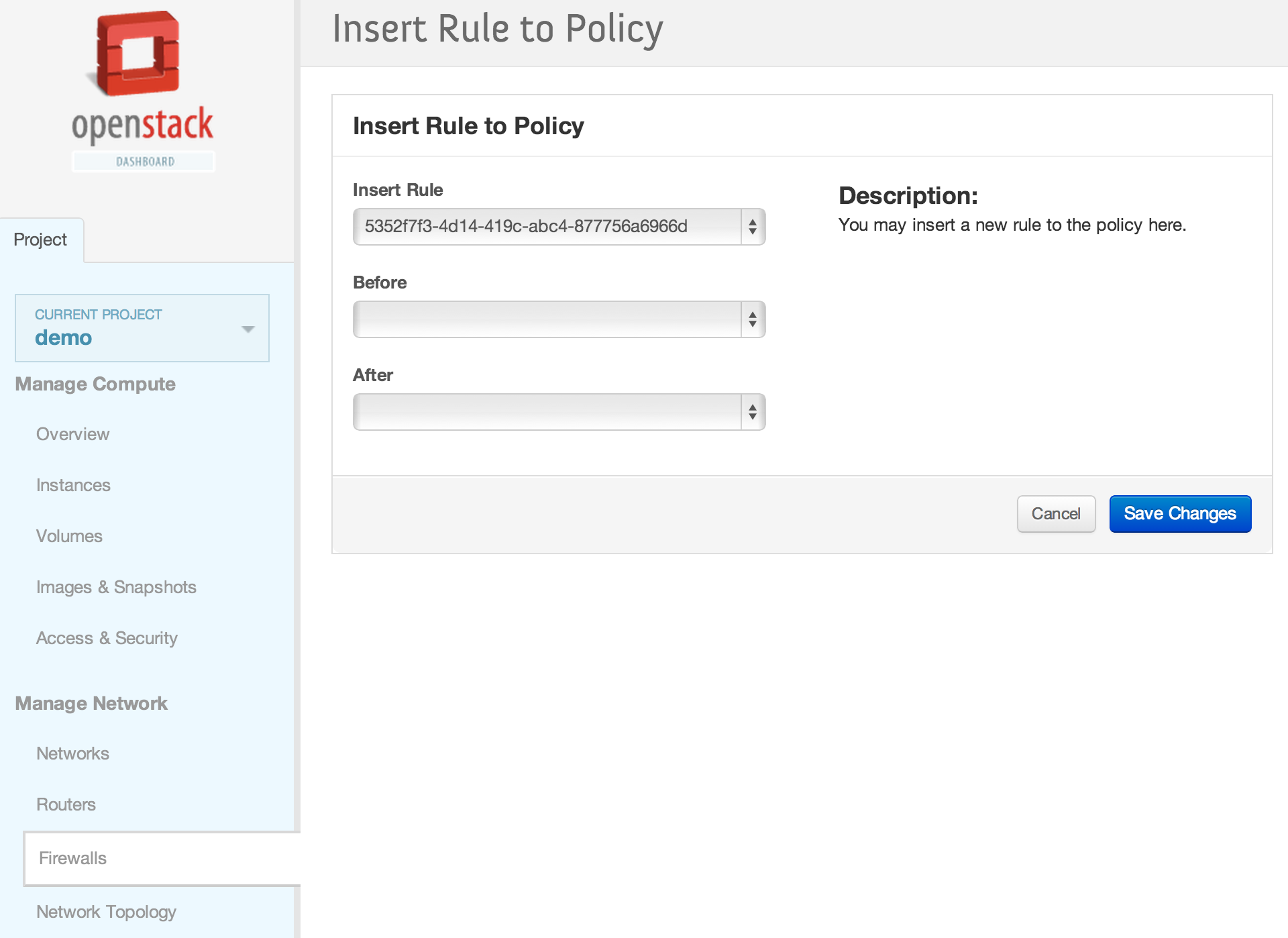
| + | [[File:2013-09-04 11.42.28 pm.png|1000x521px|framed|left|7. Insert the firewall rule into the firewall policy]] | ||
| + | <br /> | ||
| + | [[File:2013-09-04 11.43.00 pm.png|1000x521px|framed|left|8. Inserting the firewall rule in the top position]] | ||
| + | <br /> | ||
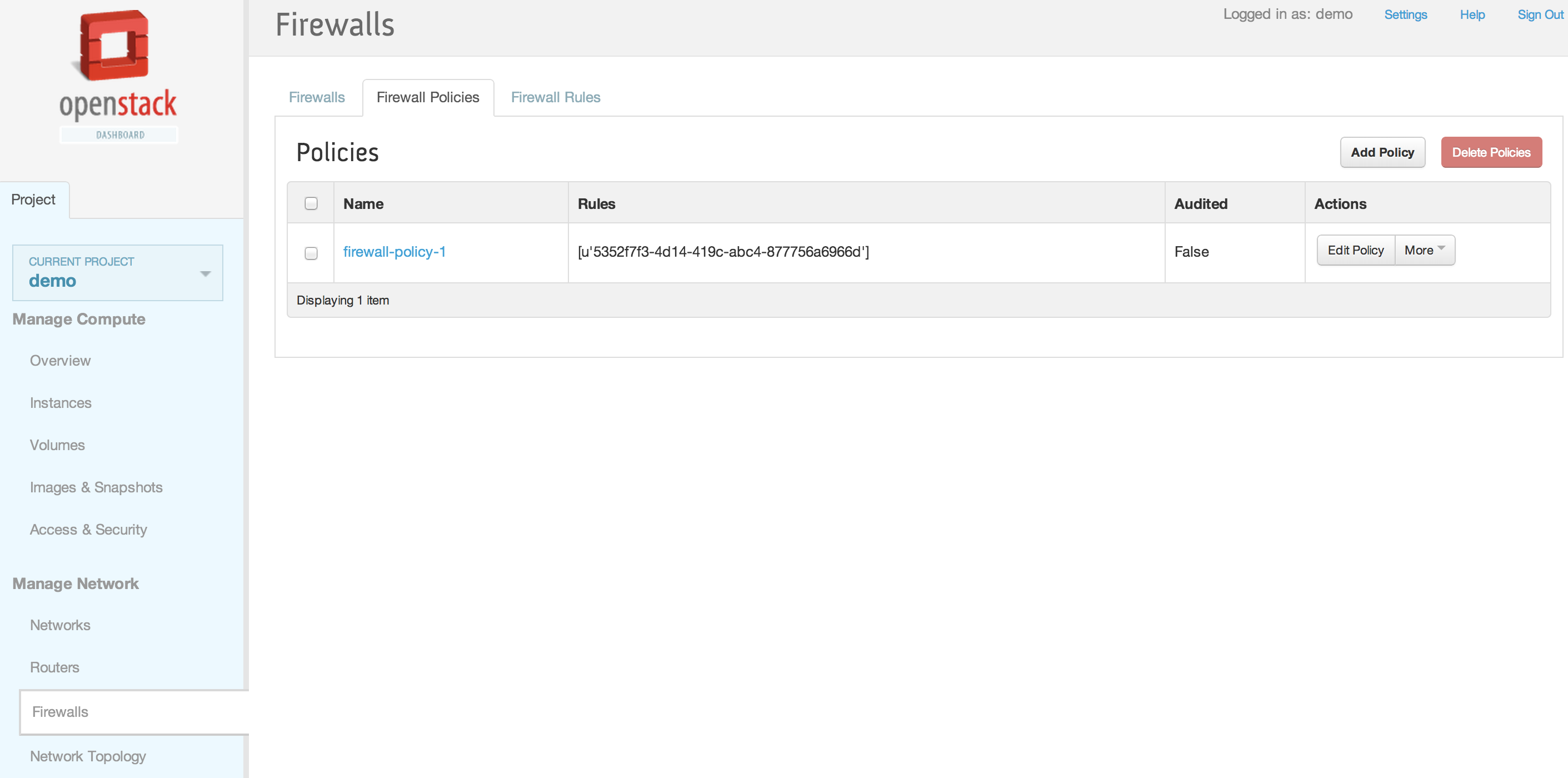
| + | [[File:2013-09-04 11.43.30 pm.png|1000x521px|framed|left|9. Firewall rule inserted into firewall policy]] | ||
| + | <br /> | ||
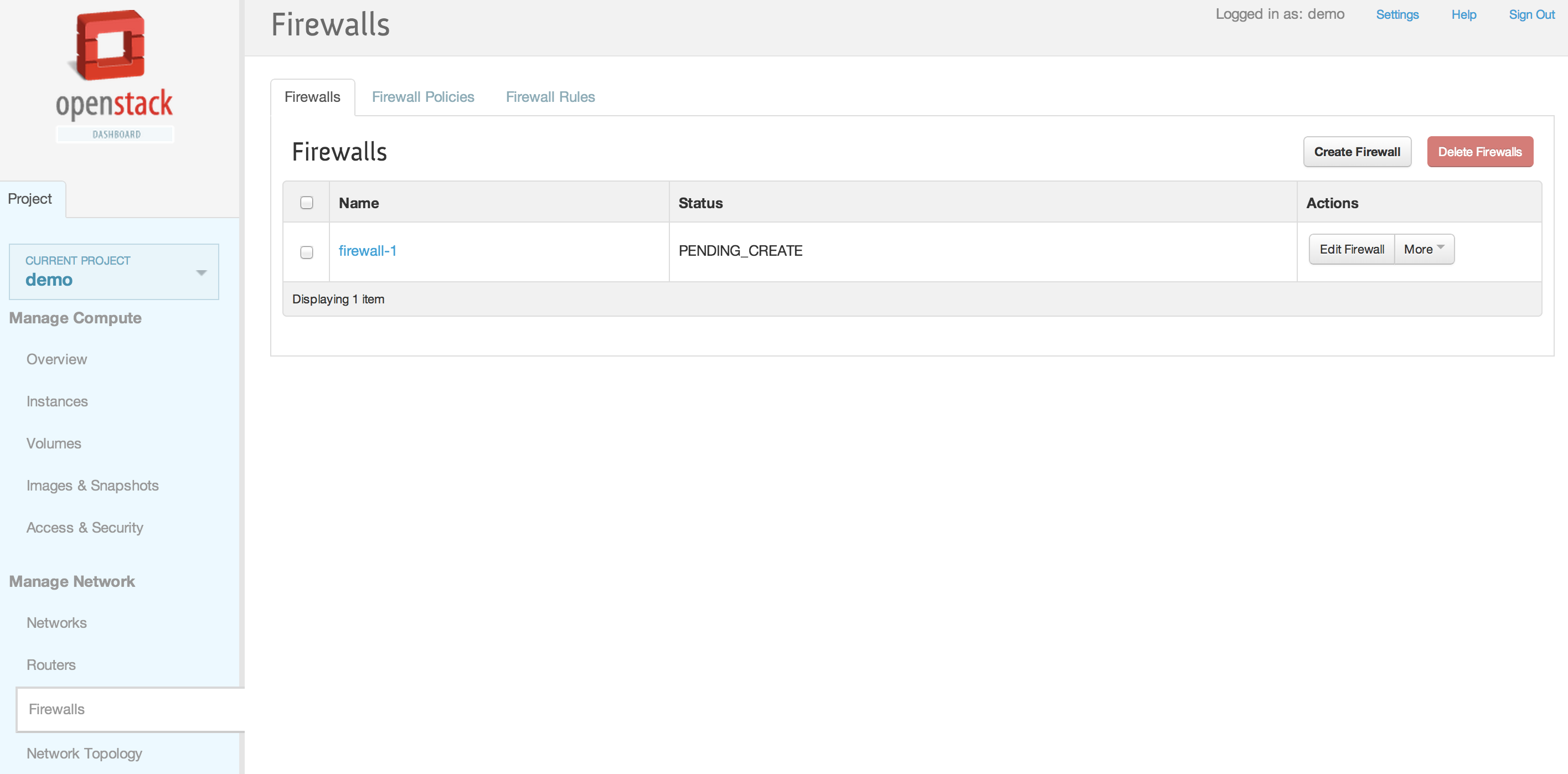
| + | [[File:2013-09-04 11.44.10 pm.png|1000x521px|framed|left|10. Firewalls tab]] | ||
| + | <br /> | ||
| + | [[File:2013-09-04 11.44.45 pm.png|1000x521px|framed|left|11. Adding a new firewall with earlier created firewall policy]] | ||
| + | <br /> | ||
| + | [[File:2013-09-04 11.45.08 pm.png|1000x521px|framed|left|12. Firewall created]] | ||
| + | <br /> | ||
| + | [[File:2013-09-04 11.45.33 pm.png|1000x521px|framed|left|13. Firewall details]] | ||
| + | <br /> | ||
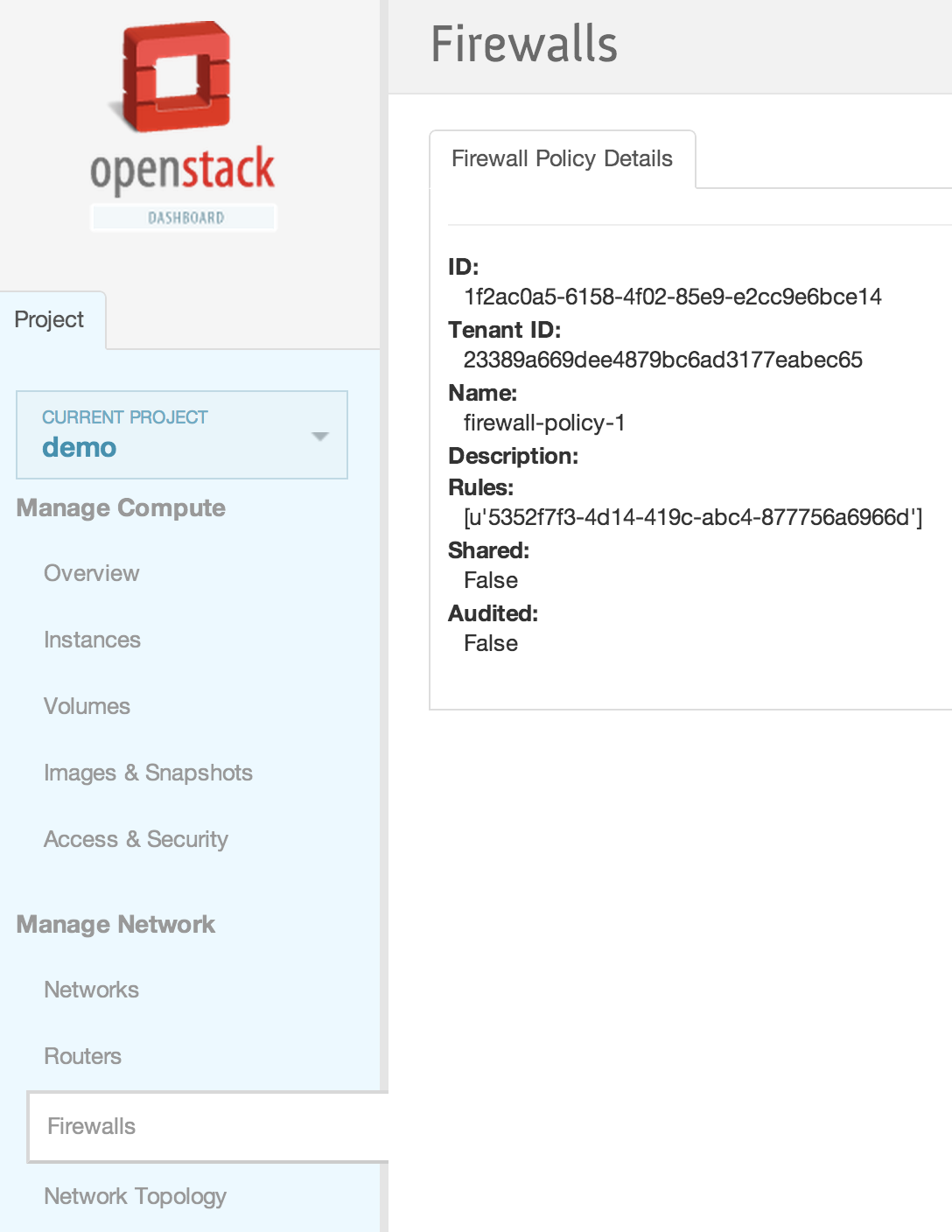
| + | [[File:2013-09-04 11.45.58 pm.png|1000x521px|framed|left|14. Firewall Policy details]] | ||
| + | <br /> | ||
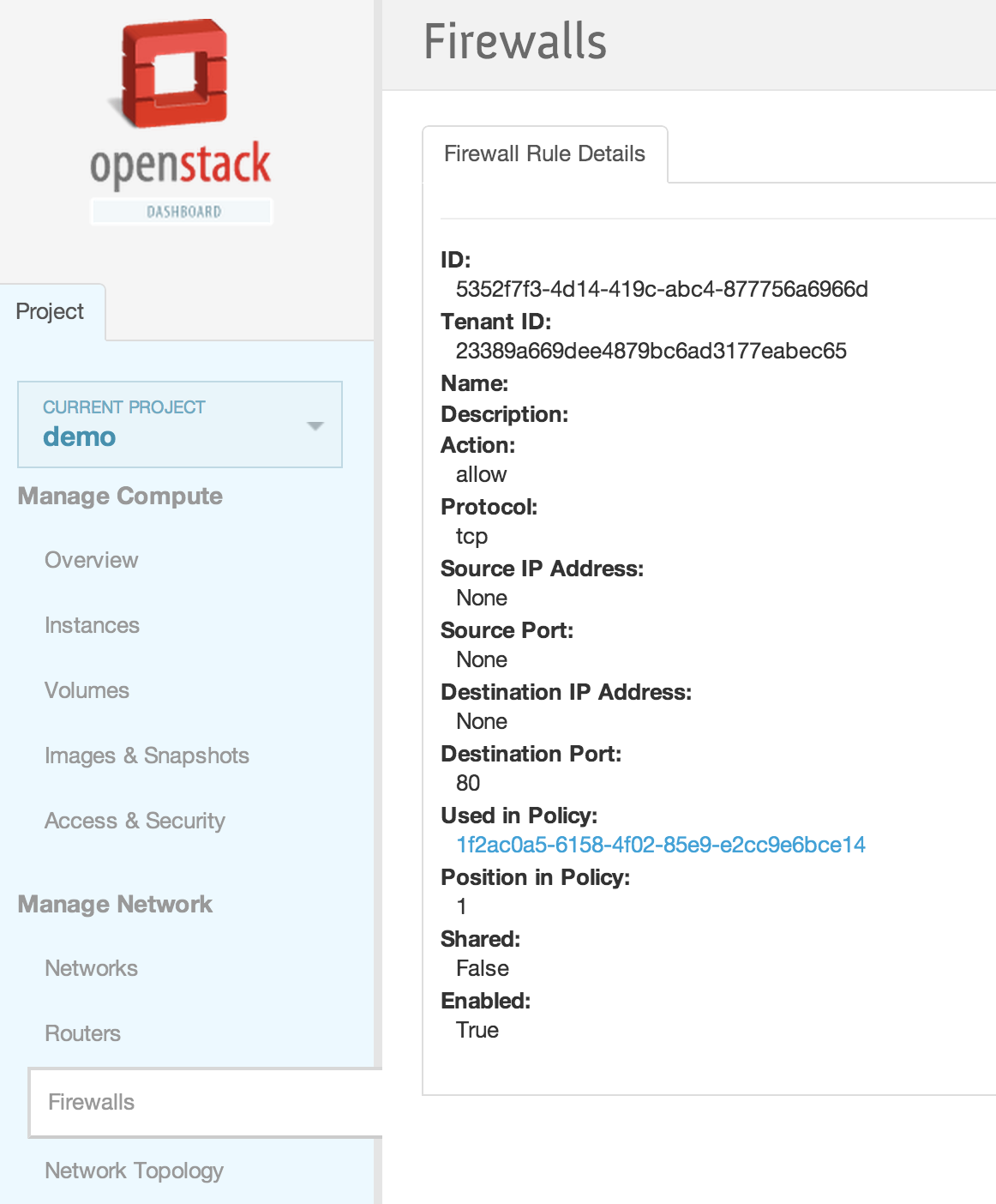
| + | [[File:2013-09-04 11.46.22 pm.png|1000x521px|framed|left|15. Firewall rule details]] | ||
Latest revision as of 22:13, 8 March 2016
Contents
Trying out FWaaS using Devstack
Add these lines in localrc:
enable_service q-fwaas
Q_SERVICE_PLUGIN_CLASSES=neutron.services.firewall.fwaas_plugin.FirewallPlugin
- The following will be populated by after the devstack installation:
/etc/neutron/l3_agent.ini
[fwaas] driver = neutron_fwaas.services.firewall.drivers.linux.iptables_fwaas.IptablesFwaasDriver enabled = True
CLI/REST Walkthrough
CLI
- To list firewalls, firewall_policies, firewall_rules:
neutron firewall-list neutron firewall-policy-list neutron firewall-rule-list
- Create firewall rule:
neutron firewall-rule-create --protocol tcp --destination-port 80 --action allow Created a new firewall_rule: +------------------------+--------------------------------------+ | Field | Value | +------------------------+--------------------------------------+ | action | allow | | description | | | destination_ip_address | | | destination_port | 80 | | enabled | True | | firewall_policy_id | | | id | 1283a548-9ca8-4a7b-a187-fc21c7fefe8e | | ip_version | 4 | | name | | | position | | | protocol | tcp | | shared | False | | source_ip_address | | | source_port | | | tenant_id | baaaf4da44874e3f82ff93beba64117e | +------------------------+--------------------------------------+
- Create firewall policy with rules:
neutron firewall-policy-create --firewall-rules "1283a548-9ca8-4a7b-a187-fc21c7fefe8e ef9fe8d1-1d79-485b-9d90-d1dd4bf228b5" test-policy Created a new firewall_policy: +----------------+--------------------------------------+ | Field | Value | +----------------+--------------------------------------+ | audited | False | | description | | | firewall_rules | 1283a548-9ca8-4a7b-a187-fc21c7fefe8e | | | ef9fe8d1-1d79-485b-9d90-d1dd4bf228b5 | | id | 257f0a59-5b16-486b-aae2-b57c60e2053f | | name | test-policy | | shared | False | | tenant_id | baaaf4da44874e3f82ff93beba64117e | +----------------+--------------------------------------+
- Create the firewall with the policy association:
neutron firewall-create 257f0a59-5b16-486b-aae2-b57c60e2053f Created a new firewall: +--------------------+--------------------------------------+ | Field | Value | +--------------------+--------------------------------------+ | admin_state_up | True | | description | | | firewall_policy_id | 257f0a59-5b16-486b-aae2-b57c60e2053f | | id | 28530399-d8ee-4700-9685-ee5d645f4d59 | | name | | | status | PENDING_CREATE | | tenant_id | baaaf4da44874e3f82ff93beba64117e | +--------------------+--------------------------------------+
- Check that the firewall is in ACTIVE state before the next operation can be performed on the firewall:
neutron firewall-show 28530399-d8ee-4700-9685-ee5d645f4d59 +--------------------+--------------------------------------+ | Field | Value | +--------------------+--------------------------------------+ | admin_state_up | True | | description | | | firewall_policy_id | 257f0a59-5b16-486b-aae2-b57c60e2053f | | id | 28530399-d8ee-4700-9685-ee5d645f4d59 | | name | | | status | ACTIVE | | tenant_id | baaaf4da44874e3f82ff93beba64117e | +--------------------+--------------------------------------+
- Delete the firewall:
neutron firewall-delete 28530399-d8ee-4700-9685-ee5d645f4d59 Deleted firewall: 28530399-d8ee-4700-9685-ee5d645f4d59
REST calls using curl:
export q_url=http://<neutron-server-ip>:9696/v2.0
for example
export q_url=http://127.0.0.1:9696/v2.0
and
export auth_token=<auth_token>
where <auth_token> is the token obtained from:
keystone token-get
or
export auth_token=`keystone token-get | awk '/id/{print $4}' | head -n1`
- To list firewalls, firewall_policies, firewall_rules:
curl -X GET -H "X-Auth-Token: $auth_token" $q_url/fw/firewalls | python -mjson.tool curl -X GET -H "X-Auth-Token: $auth_token" $q_url/fw/firewall_policies | python -mjson.tool curl -X GET -H "X-Auth-Token: $auth_token" $q_url/fw/firewall_rules | python -mjson.tool
- Create firewall rule:
curl -X POST -H "X-Auth-Token: $auth_token" -H "Content-type:application/json" -d '{"firewall_rule": {"protocol": "tcp", "destination_port": "80", "action": "allow"}}' $q_url/fw/firewall_rules
- Create firewall policy:
curl -X POST -H "X-Auth-Token: $auth_token" -H "Content-type:application/json" -d '{"firewall_policy": {"name": "fwasspolicy"} }' $q_url/fw/firewall_policies
- Add rule to policy (this could have been done while creating the firewall policy too):
curl -X PUT -H "X-Auth-Token: $auth_token" -H "Content-type:application/json" -d '{"firewall_policy": {"firewall_rules": ["1d47c609-8fd1-4aad-97fd-157887c47b4f"]}}' $q_url/fw/firewall_policies/9c50d2d0-3a85-4ed7-a20f-bef8c08233e3
- Create the firewall with the policy association:
curl -X POST -H "X-Auth-Token: $auth_token" -H "Content-type:application/json" -d '{"firewall": {"name": "fwasstest", "firewall_policy_id": "9c50d2d0-3a85-4ed7-a20f-bef8c08233e3"} }' $q_url/fw/firewalls
- Delete the firewall:
curl -X DELETE -H "X-Auth-Token: $auth_token" $q_url/fw/firewalls/9649548e-b87f-4c56-bbb7-5ee84b316da1
Horizon Interface