Difference between revisions of "Isolated-network"
(→network) |
(→subnet) |
||
| Line 63: | Line 63: | ||
=== subnet === | === subnet === | ||
* isolated_network:arp_proxy_mac | * isolated_network:arp_proxy_mac | ||
| − | :Set the MAC address of the promiscuous port (gateway). It's a ''String'' and by default, it sets to ''None''. When it's ''None'', the promiscuous port is disabled (No local proxy APR activated on the gateway) and when it sets, the promiscuous port is enabled (a local proxy ARP is activated on the gateway interface | + | :Set the MAC address of the promiscuous port (gateway). It's a ''String'' and by default, it sets to ''None''. When it's ''None'', the promiscuous port is disabled (No local proxy APR activated on the gateway) and when it sets, the promiscuous port is enabled (a local proxy ARP is activated on the gateway interface, flows to that MAC address are authorized to go through ports of the network and broadcast ARP are DNATed to that MAC address) |
Revision as of 08:24, 24 May 2013
Contents
Overview
When a network is created, a broadcast domain is available to plug ports. It should be interesting to proposed an option on the network creation that enable the isolation between ports in a same broadcast domain (network), similar to a common use of private VLANs with isolated port technologies (RFC 3069 and RFC 5517). This prevents communication between VMs on the same logical switch. The promiscuous port will be the gateway port by default. And if we want, we can authorize the traffic between port through a local proxy ARP/NDP.
Use Cases
This functionality could address the use cases where we create a shared network between tenants, for example. And this should also works with a provider network, if we want to create shared provider network to carry the public access in our Cloud for all tenants.
Possible implementation
IPv4 and/or Local proxy ARP
- ARP broadcast modifies to unicast MAC address of the local APR proxy (gateway) when it defines.
- Multicast bootp traffic modifies to unicast MAC address of the DHCP agent when it defines
- Authorize traffic for the gateway MAC address if it defines
- Drop all other traffic
When a network is created, a boolean can specify if it's isolated. And when a gateway is added to the network, a boolean can enable a local proxy ARP on the gateway to enable l3 traffic between the ports.
Note: If the gateway and local proxy ARP port aren't managed by Quantum (on a provider network for example), it could be possible to define trough the API (on subnet creation for example) the MAC address of the gateway/local proxy ARP.
Note: It's not sure that the local proxy ARP must be handled by the gateway. If not, we can imagine implement the local proxy ARP by a new agent with a dedicated IP.
Technical implementation
Local Proxy ARP
The Linux kernel proposes the possibility to enable a proxy ARP which can replies back to the same interface (/proc/sys/net/ipv4/conf/<interface>/proxy_arp_pvlan)
Flows
With OVS driver in tunneling mode we can use the open flow tools to NAT flows with mod_dl_dst action and drop flows with drop action.
ebtables
With LB driver and the OVS driver in VLAN mode, we can use Linux-based bridging firewall ebtables
IPv6 Proxies NDP messages
Not yet define but actually, the OpenStack networking l3 agent does not support IPv6
Implementation plan
The implementation of this extension will roughly follow the next plan:
- API modifications and database model with related code
- Implement support of proxy ARP on the L3 agent
- Implement support in OVS plugin
- Implement support in LB plugin
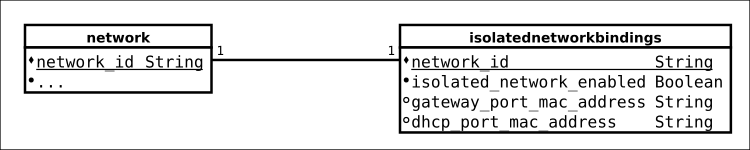
Data Model Changes
The database model extension is shown in the diagram below. It adds two new tables to the quantum database of the plugin.
- To binding the activation of the isolated function with a network;
- To binding the activation of the promiscuous port on the subnet. If a MAC address is provide, the promiscuous port on the subnet is activated.
Configuration Variables
N/A
API’s
The isolated network extends the Quantum API by creating new attributes. No new resources or actions are defined.
Extended attributes
The network and subnet structures will be extended with one new attributes each in the isolated network namespace:
network
- isolated_network:enabled
- Enable or disable the isolation of ports on the network. It's a 'Boolean' and by default, it sets to 'False'. When it disabled all traffics are authorized to go through the port and when it enabled, broadcast and multicast are dropped (except bootp).
subnet
- isolated_network:arp_proxy_mac
- Set the MAC address of the promiscuous port (gateway). It's a String and by default, it sets to None. When it's None, the promiscuous port is disabled (No local proxy APR activated on the gateway) and when it sets, the promiscuous port is enabled (a local proxy ARP is activated on the gateway interface, flows to that MAC address are authorized to go through ports of the network and broadcast ARP are DNATed to that MAC address)