Difference between revisions of "Horizon/DomainWorkFlow"
Dan Nguyen (talk | contribs) m (→Workflow 1. Cloud Admin creates a new Domain and Resources) |
Dan Nguyen (talk | contribs) |
||
| Line 54: | Line 54: | ||
* User (_member_ role) | * User (_member_ role) | ||
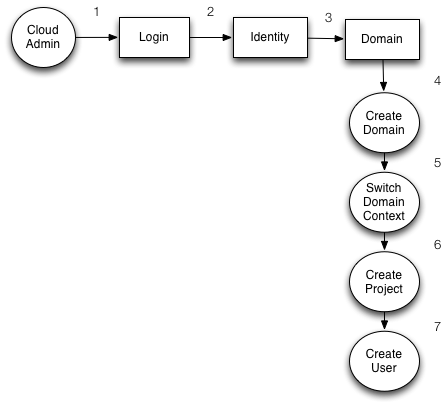
| − | === Workflow 1. Cloud Admin | + | === Workflow 1. Cloud Admin sets a Domain Context === |
[[File:Switch-domain-workflow-1.png]] | [[File:Switch-domain-workflow-1.png]] | ||
| + | |||
| + | ==== Cloud Admin Logs in ==== | ||
| + | [[File:1. Log In.png]] | ||
| + | ==== Cloud Admin navigates to the Identity Dashboard and Domain panel ==== | ||
| + | [[File:2. Identity-Domains.png]] | ||
| + | ==== Cloud Admin impersonates a Domain or switches Domain context ==== | ||
| + | [[File:3. Set Domain Context.png]] | ||
Revision as of 00:47, 13 January 2015
Intro
This wiki describes how to enable Domain Scoped Token support in Horizon and how to navigate the existing work flows.
Prerequisites
devstack
You'll need to have keystone running in a VM or somewhere you can reach it from Horizon.
keystone policy.json file
You can start testing with the default /etc/keystone/policy.json file but at some point you will want to switch in the following file: https://github.com/openstack/keystone/blob/master/etc/policy.v3cloudsample.json
memcached
- Memcached should be installed and running (perhaps on the same host as horizon to keep things simple)
- The memcached client library needs to be installed in horizon's venv (python-memcached==1.53)
- Horizon needs to be configured to use memcached
local_settings.py
...
# We recommend you use memcached for development; otherwise after every reload
# of the django development server, you will have to login again. To use
# memcached set CACHES to something like
CACHES = {
'default': {
'BACKEND': 'django.core.cache.backends.memcached.MemcachedCache',
'LOCATION': '127.0.0.1:11211',
}
}
SESSION_ENGINE = 'django.contrib.sessions.backends.cache'
...
keystone v3
Horizon needs to be configured to use keystone v3 and multi domain support
local_settings.py
...
OPENSTACK_API_VERSIONS = { "identity": 3, }
OPENSTACK_KEYSTONE_MULTIDOMAIN_SUPPORT = True
OPENSTACK_KEYSTONE_URL = "http://%s:5000/v3" % OPENSTACK_HOST
...
django-openstack-auth
You'll need to pull down this patch to be able to retrieve a domain scoped token from the http session. https://review.openstack.org/#/c/141153/
Cloud Admin account in keystone
One way to enable this account to grant your admin user access to the 'default' domain. If a user has an 'admin' role and access to the 'default' domain then they are considered to be a Cloud Admin.
Users
This page only considers three users
- Cloud Admin
- Domain Admin
- User (_member_ role)